The Overlooked Connection
Two Worlds That Don’t Talk
In most organizations, ICT assets and business processes live in different universes. The IT team maintains an inventory of servers, laptops, and SaaS applications. Meanwhile, operations or compliance departments track workflows like onboarding new customers or processing payroll. The problem? These two lists rarely meet.
The Blind Spots It Creates
When the bridge between technology and processes is missing, risk management becomes a guessing game. Blind spots quickly appear:
- Resilience gaps: You can’t protect what you don’t know is critical.
- Compliance headaches: Regulations like NIS2 and DORA expect visibility of dependencies—but auditors often find none.
- Continuity risks: A single outage can snowball if no one knows which processes rely on which systems.
A Simple Example
Imagine your CRM goes down for half a day. On the surface, it looks like an IT incident. In reality, sales operations grind to a halt, revenue forecasts become unreliable, and customer relationships take a hit. The real problem wasn’t the outage in itself, rather than the fact that the CRM’s link to sales processes was never identified and documented.
Why This Mapping Matters
Create Clarity
Mapping ICT assets to business processes is the difference between reacting blindly to incidents and making informed, confident decisions. Without the map, every outage or security incident leads to difficult (if not impossible) detective work. With it, you immediately know what’s going on and how to react.
Four Big Reasons It Matters
-
Risk assessment becomes real
A risk register full of generic “server failures” or “system outages” doesn’t tell you much. Tie those risks to the payroll process or online ordering system, and suddenly the business impact is crystal clear. -
Incident response gets sharper
When a system goes down, the first question is: who feels it? Mapping answers that instantly, shaving precious hours off recovery. -
Compliance stops being a checkbox
Regulations like NIS2, DORA, and GDPR increasingly demand clarity around ICT dependencies. Having a living map becomes regulatory insurance. -
Board-level conversations improve
Telling executives “the ERP is at risk” gets blank stares. Telling them “if the ERP fails, order fulfillment stops” gets attention—and budget.
A Strategic Advantage
Organizations that take this seriously gain more than compliance points. They earn the ability to translate IT risk into business language, which is what truly resonates with decision-makers. This makes IT less about technology, and more about business support.
The Pitfalls Most Companies Face
Why Good Intentions Fall Short
Plenty of organizations set out to connect their ICT assets with business processes. Yet somewhere between the kickoff meeting and the first audit, the effort fizzles. The reasons are surprisingly consistent.
The Usual Suspects
-
Siloed ownership
IT owns the systems, business units own the workflows, but nobody owns the relationship between the two. It’s like two departments speaking different languages without a translator. -
Static documentation
Excel sheets, Visio diagrams, or PDFs look neat for a few weeks. Then updates happen—new SaaS tools, process tweaks, a system decommission—and the map is outdated before the ink is dry. -
Overengineering the exercise
Some teams try to capture every mouse click and every asset, creating a mountain of detail that no one can realistically maintain. The result? Frustration and abandonment.
The Consequences
When mapping efforts collapse, the business ends up with a false sense of security. Leaders believe the documentation exists and is reliable, only to discover during an incident—or during an audit—that it’s incomplete or obsolete. At that point, it’s not just a gap. It’s a liability.
A Practical Framework for Mapping
Start Where It Hurts Most
The temptation is to map everything—but that’s a trap. Instead, begin with critical business processes: the ones that, if they fail, the organization stalls. For a bank, that might be payment processing. For a hospital, patient care systems. For an online retailer, the checkout flow.
Link Only What Matters
Not every laptop or shared folder deserves a place on the map. Focus on the essential ICT assets that keep those critical processes alive. A good test is to ask: If this system failed, would the process stop? If the answer is yes, it belongs in the mapping.
Use Tiers of Impact
Not all dependencies carry the same weight. Classify them to avoid “everything is critical” syndrome:
- Critical – Without it, the process halts immediately.
- Important – Disruption slows the process but doesn’t stop it.
- Supportive – Useful, but the process limps along without it.
This layered view helps prioritize resilience investments instead of spreading resources too thin.
Keep It Alive
The most elegant map is useless if it’s outdated. Build updates into change management: every time a new system is introduced, retired, or significantly modified, the map gets adjusted. Treat it as a living asset, not a one-time compliance project.
A Tool, Not a Burden
Done right, this framework reduces complexity instead of adding it. It gives CISOs and DPOs a clear, business-centric view of risk that can evolve with the organization, rather than gathering dust in a folder.
The Value for CISOs and DPOs
Why CISOs Care
For CISOs, mapping ICT assets to business processes provides a clear, business-aligned view of risk. Instead of drowning in technical details, they can:
- Prioritize security investments based on actual business impact.
- Build a risk register that resonates with executives.
- Identify single points of failure before attackers or outages do.
- Justify budgets by showing how technology failures directly disrupt revenue or operations.
Why DPOs Care
For DPOs, the same mapping exercise becomes a privacy control mechanism. By tying ICT assets to processes, they can:
- Pinpoint exactly where personal data is processed and stored.
- Simplify GDPR reporting and DPIAs with reliable documentation.
- Spot risks in cross-border data transfers or vendor dependencies.
- Ensure that privacy obligations are linked to the business processes that generate them.
One Map, Different Uses
The beauty of this approach is that the same mapping serves both functions, even if the two roles never sit in the same room. For CISOs, it’s about resilience and security. For DPOs, it’s about compliance and data protection. Different lenses, same foundation.
Making It Work with Brainframe GRC
From Theory to Execution
By now, it’s clear that mapping ICT assets to business processes is a necessity. The challenge is keeping that mapping alive. Spreadsheets, Visio diagrams, or one-off workshops quickly turn stale, leaving teams back at square one. That’s where Brainframe GRC steps in.
How Brainframe GRC Closes the Gap
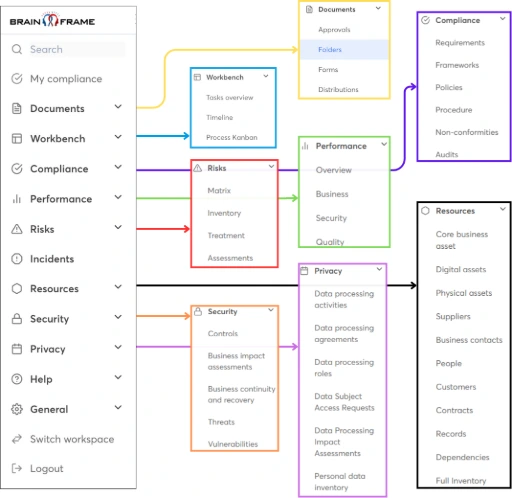
Brainframe GRC transforms the idea of mapping into a living, breathing part of governance:
- Centralized visibility: ICT assets, risks, and business processes all live in one platform instead of scattered across documents.
- Visual dependencies: You can click on any of your business processes, and show the IT assets, policies and procedures, or risks associated with it.
- Asset hierarchy: For each asset supporting a business process you can configure the underlying assets that support the core business assets, offering a hierarchical view and ensuring you don’t miss any dependency.
- Impact-driven risk registers: Risks aren’t abstract—they’re tied directly to the processes that matter most to the business.
More Than Compliance
Brainframe GRC ensures your mapping exercise doesn’t collect dust after an audit. It becomes a working asset used in:
- Tabletop exercises and incident response planning.
- Business continuity and disaster recovery strategies.
- Board reporting, where executives finally see cyber risks in business terms.
The Real Value
Instead of juggling static documents or piecing together half-finished maps, Brainframe GRC gives organizations a single, reliable source of truth. It makes ICT–process mapping actionable—turning what was once a forgotten link into a strategic advantage.