Why Project Management Matters
There was a time when project management meant keeping deadlines straight and making sure budgets didn’t mysteriously evaporate halfway through. Those days are long gone. As organizations accelerate their digital transformations, project managers find themselves operating in an environment where security threats and regulatory demands are just as critical as timelines and deliverables.
From IT rollouts to security-critical initiatives
The nature of projects has shifted. No longer are we talking about simple hardware upgrades or basic network deployments; today’s initiatives involve:
- Cloud migrations where sensitive customer data moves across jurisdictions.
- Banking applications that must operate in real time under strict regulatory requirements and supervision.
- AI-driven tools that introduce new risks like model poisoning and data leakage.
On top of being technology upgrades; these are business-critical transformations that demand tight control over security and compliance at every stage.
The threat factor: supply chain, ransomware, and beyond
Cyber threats have become project risks in their own right. A supply chain compromise during deployment can introduce backdoors before a system even goes live. A ransomware attack mid-migration can halt progress entirely, forcing teams into costly recovery. Without security baked into the project plan, the consequences are immediate:
- Delays and budget overruns caused by incident response efforts.
- Compromised deliverables where security flaws surface after launch.
- Regulatory penalties if controls fail to meet mandated standards like ISO 27001 or DORA.
Regulations raising the bar
Global regulations are setting higher expectations for project governance:
- DORA (Digital Operational Resilience Act) for financial services in the EU.
- NIS2 for operators of essential services, from healthcare to energy.
- ISO 27001 and GDPR as cross-industry benchmarks for security and privacy.
These frameworks require structured oversight, documented risk assessments, and verifiable controls — all of which must be built into the project lifecycle rather than stuck on at the end.
Why every industry should care
Although banking and finance face the sharpest scrutiny, the reality is universal. SaaS startups managing customer data, healthcare providers digitizing patient records, and manufacturers rolling out connected factories all face the same challenge: security missteps in projects translate to operational and reputational crises.
Core Elements of Good Project Management
Good project management is built on four classic pillars: Scope, Time, Cost, and Quality. But in the current landscape, those four are no longer enough. A fifth pillar, Security, now demands equal attention. Without it, even a project that meets deadlines and budgets can become a liability, particularly when handling sensitive data or building critical infrastructure.
Defining roles and responsibilities
Successful projects start with clear accountability. For cybersecurity-sensitive initiatives, this often extends beyond the traditional project team:
- Project Manager – Oversees timelines, deliverables, and cross-team coordination.
- CISO or Security Lead – Ensures security objectives and controls are embedded from day one.
- Technical Leads – Translate security requirements into system architecture and code.
- Compliance Officers / Risk Managers – Monitor adherence to frameworks like ISO 27001, DORA, or PCI DSS.
- Vendors and Suppliers – Must align with the organization’s security and regulatory standards, often verified through questionnaires or audits.
Clear roles prevent gaps where security responsibilities fall through the cracks — a frequent cause of vulnerabilities discovered late in a project.
Phases of a secure project lifecycle
Each project phase ties closely to security activities. Neglecting these early usually results in costly remediation later.
1. Initiation
- Identify critical assets (e.g., payment data, personal health records).
- Define security objectives alongside business goals (e.g., encryption standards, resilience targets).
- Determine regulatory scope — are GDPR or PCI DSS in play?
2. Planning
- Conduct risk assessments to anticipate threats and assign mitigation plans.
- Incorporate security milestones into the project schedule (penetration tests, audits).
- Align with frameworks (ISO 27001 Annex A, NIST 800-53) for control mapping.
3. Execution
- Enforce secure development practices (code reviews, static/dynamic testing).
- Vet and manage vendors — ensuring supply chain security (e.g., SOC 2 reports).
- Control changes: every configuration update should undergo security review.
4. Monitoring
- Perform continuous testing and auditing to catch vulnerabilities mid-project.
- Track threat intelligence relevant to the project (e.g., zero-day affecting a chosen library).
- Monitor KPIs like mean time to detect and remediate security issues.
5. Closure
- Conduct post-mortems to capture lessons learned and improve future projects.
- Archive documentation for audit and compliance evidence.
- Ensure all security controls are operationalized, not just implemented on paper.
When security changes the risk equation
Traditional project risks — scope creep, vendor delays, budget overruns — take on a new edge when cybersecurity is involved:
- A delayed vendor can become a supply chain risk if their security posture weakens over time.
- Scope creep can unintentionally add features that introduce new attack surfaces (e.g., adding APIs without proper authentication).
- Cost overruns may force security trade-offs, such as delaying encryption upgrades or skipping penetration tests — decisions that can backfire under regulatory oversight.
Cybersecurity-Specific Challenges in Projects
Even with strong project management fundamentals, cybersecurity introduces a set of complications that traditional methods rarely anticipate. Timelines stretch, risk registers balloon, and the “just get it live” mentality can collide head-on with the need for secure practices.
1. Threats evolve faster than project timelines
A typical project plan might span six months to a year; attackers innovate weekly. By the time a system nears deployment, the threat landscape can look entirely different. For example:
- A library considered safe at planning can be flagged for critical vulnerabilities mid-execution.
- A sudden surge in ransomware-as-a-service offerings can raise the project’s threat profile overnight.
This forces teams to revisit risk assessments continuously rather than treating them as static documents.
2. Legacy systems: the stubborn reality
Most projects don’t start with a clean slate. Banks, hospitals, and manufacturers alike rely on legacy infrastructure that’s deeply integrated into operations. Modernizing these environments without breaking them — or introducing new risks — is notoriously challenging:
- Older systems may lack patch support or encryption, forcing compensating controls.
- Integration often requires workarounds that expand the attack surface (e.g., exposing APIs to bridge old and new systems).
3. Third-party dependencies
Modern projects rarely stay in-house. Cloud providers, SaaS platforms, consultants, and specialized vendors are central to execution. But every external dependency adds a supply chain risk:
- Vendors might have weaker security postures, making them targets.
- Breaches at a single partner can cascade, as seen in recent software supply chain attacks (e.g., SolarWinds).
- Vendor lock-in complicates response plans if security flaws are discovered late in the process.
4. Compliance overload
Cybersecurity projects often trigger multiple regulatory obligations simultaneously. For instance, a new core banking platform might need to address:
- ISO 27001 for security controls.
- DORA for operational resilience.
- PCI DSS for payment card data.
- GDPR for personal data protection.
Navigating overlapping frameworks can create compliance fatigue, especially when audit evidence must be collected for each.
5. Conflicting stakeholder priorities
Business units want speed and features; security teams prioritize risk reduction. This friction often surfaces as:
- Pushback on security controls viewed as slowing development (e.g., multi-factor authentication during testing).
- Budget disputes where security hardening is seen as “extra” rather than essential.
- Communication breakdowns that result in security being treated as an afterthought instead of a design requirement.
6. Documentation and evidence burden
Every security decision in a project must be documented: risk assessments, control mappings, test results, approvals. In high-regulation sectors like banking or healthcare, this can easily generate hundreds of artifacts. Without centralization, teams end up buried in spreadsheets, version conflicts, and email threads — a nightmare when auditors come knocking.
Practical Strategies for Securing Projects
Theory is nice, but projects live and die by execution. Security has to be embedded into every phase, or teams end up firefighting vulnerabilities long after launch. Here are strategies that keep security visible — and manageable — without grinding momentum to a halt.
1. Start with security on day one
Security goals should sit alongside business objectives in the project charter. Examples:
- Define what data is sensitive and how it must be protected (e.g., encryption in transit and at rest).
- Decide early whether the project needs certifications (ISO 27001, SOC 2) or compliance mappings (DORA, NIS2).
- Appoint a security champion in the project team to keep the conversation active during design decisions.
2. Make risk assessments a living document
Most projects do a risk assessment once, file it away, and never revisit it. That doesn’t work for cybersecurity:
- Reassess risks at major milestones (e.g., after vendor selection, before go-live).
- Include emerging threats from threat intelligence feeds or regulatory advisories.
- Track risks that evolve during execution, like newly discovered vulnerabilities in chosen tools.
3. Tighten vendor and third-party oversight
Supply chain risk is now one of the top failure points in cybersecurity projects:
- Vet vendors using structured questionnaires or recognized frameworks (e.g., SIG Lite, CSA CAIQ).
- Require evidence of security controls, such as ISO 27001 reports.
- Include security clauses in contracts: breach notification timelines, right to audit, minimum control baselines.
4. Control changes as if they were new risks
Projects rarely run as originally scoped. Every new feature or integration point is a potential attack surface:
- Require change requests to include a security impact assessment.
- Conduct mini threat modelings when introducing new APIs or workflows.
- Document and approve each change, so nothing slips through informally.
5. Prepare for the worst — crisis readiness
Even the best projects face incidents during rollout. Plan responses rather than improvising:
- Create incident response templates tailored to the project (e.g., compromised test environment, vendor outage).
- Assign communication responsibilities — who informs regulators, customers, and executives?
- Run tabletop exercises to ensure readiness, especially in regulated industries like banking or healthcare.
6. Measure and report security metrics
Without metrics, security work becomes invisible. Examples of project-level KPIs:
- Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) during testing or rollout.
- Percentage of high-severity risks mitigated before go-live.
- Number of vendor findings resolved before integration.
Reporting these metrics helps stakeholders see security as a value driver.
Frameworks and Standards that Guide Secure Project Management
When projects involve sensitive data or critical operations, improvisation isn’t an option. Established frameworks and standards provide the structure needed to keep security integrated from planning to post-launch. The challenge is knowing which ones apply and how to combine them without drowning in paperwork.
ISO 27001: The anchor for most industries
- Provides a risk-based approach to information security management.
- Its Annex A controls (e.g., supplier management, change control, incident response) map neatly onto project phases.
- Often forms the baseline for audits — even when other frameworks (like PCI DSS or DORA) are layered on top.
- Especially valuable in multi-project environments where consistent controls must be applied across teams.
ISO 21502: The dedicated project management standard
- Focuses on governance, planning, and execution of projects in any industry.
- Emphasizes roles, responsibilities, and stakeholder engagement — essential when cybersecurity teams, compliance officers, and vendors must collaborate.
- Provides guidance on aligning project objectives with organizational strategy, which fits well when projects are part of broader security or resilience programs (e.g., ISO 27001 certification efforts).
- Useful for mature organizations seeking formal project management frameworks that integrate easily with security requirements.
DORA (Digital Operational Resilience Act)
- Mandatory for EU financial institutions.
- Focuses on ICT risk management and resilience: operational continuity, testing, and third-party oversight.
- Forces project managers in finance to consider not just security, but recovery and resilience from day one.
NIS2 Directive
- Applies to operators of essential and important services across the EU (e.g., energy, healthcare, financial services).
- Imposes stringent cybersecurity and reporting obligations, including incident response planning.
- Project teams must incorporate NIS2 requirements into design and execution phases, especially for critical infrastructure projects.
How these frameworks work together
Rarely does a project answer to just one framework. A banking cloud migration might simultaneously involve:
- ISO 27001 for overarching ISMS structure.
- ISO 21502 for structured project governance.
- DORA for operational resilience and ICT risk.
- NIS2 for broader cybersecurity requirements and incident reporting.
- GDPR for customer data privacy.
Mapping controls across these avoids duplication and ensures that one security activity (like encryption verification) satisfies multiple obligations.
Where Brainframe Fits In
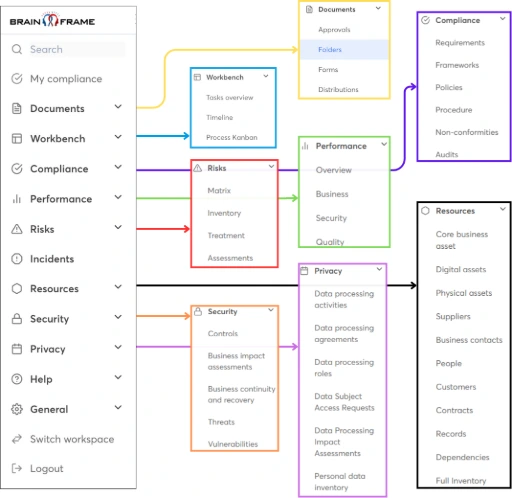
Brainframe makes security in project management practical. Many teams know they should map risks, track controls, and keep documentation audit‑ready, but in reality? That work ends up somewhere across spreadsheets, emails, and half‑updated SharePoint folders. This is where Brainframe helps turn structured theory into something usable.
A single workspace for security and project oversight
Brainframe provides a central hub where all project stakeholders — from project managers to CISOs and compliance officers — work off the same information. Instead of juggling multiple tools, teams can:
- Link security objectives directly to project milestones.
- Assign tasks and approvals to the right people, with built‑in reminders.
- Maintain an audit trail of changes, decisions, and evidence automatically.
For projects under ISO 21502 governance and aligned with ISO 27001 or NIS2, this single view simplifies reporting and reduces duplicated effort.
Integrated risk and compliance management
Every cybersecurity‑sensitive project involves risk. Brainframe lets teams:
- Update risk management dynamically as the project evolves.
- Map risks to specific frameworks like DORA, PCI DSS, or ISO 27001 Annex A controls.
- Visualize project risk posture with real‑time dashboards, making it easier to communicate with executives and regulators.
Vendor oversight without the chaos
Critical projects — especially in banking and healthcare — rely on vendors for cloud services, APIs, or development. Brainframe centralizes this by:
- Sending security questionnaires to vendors and tracking responses in‑platform.
- Storing certifications (ISO 27001, PCI DSS).
- Linking vendor risks to overall project risks, so nothing slips through unnoticed.
Evidence and documentation, done right
Instead of chasing attachments and hunting through emails during audits, Brainframe lets teams:
- Attach policies, test results, and approvals directly to project tasks.
- Version‑control documents so regulators see exactly what was in place at each stage.
- Smoothen the audit process by allowing you to make your documentation available to your auditors directly inside the tool, without having to run after the owner of each piece of information one by one.
By consolidating these elements, Brainframe allows teams to focus on delivering secure, compliant outcomes rather than getting lost in the administrative burden.