Brainframe GPTs
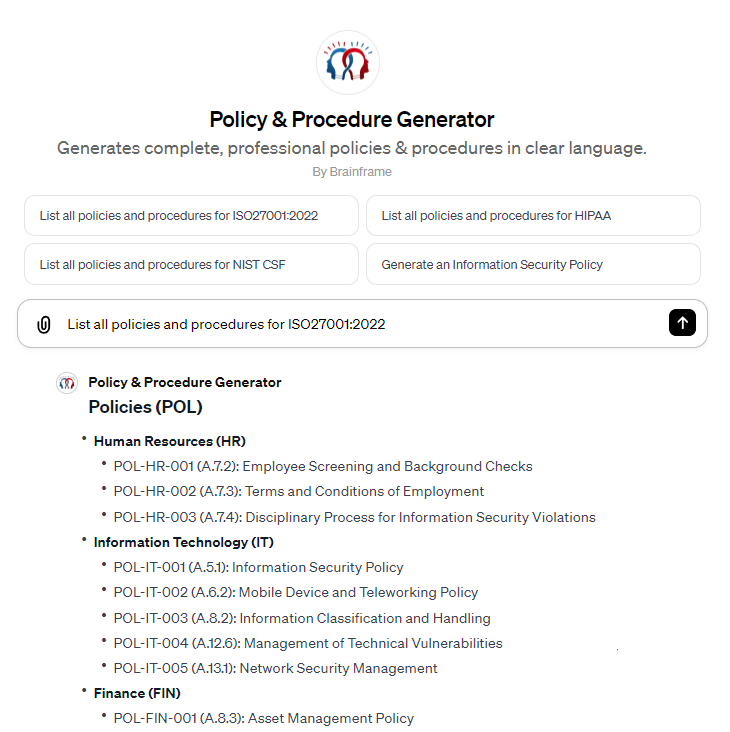
Policy & Procedure generator
Nobody should be wasting time on reinventing the wheel, which is why we created a GPT* to generate lists of required policies and procedures and their content in line with the requirements you need to implement.
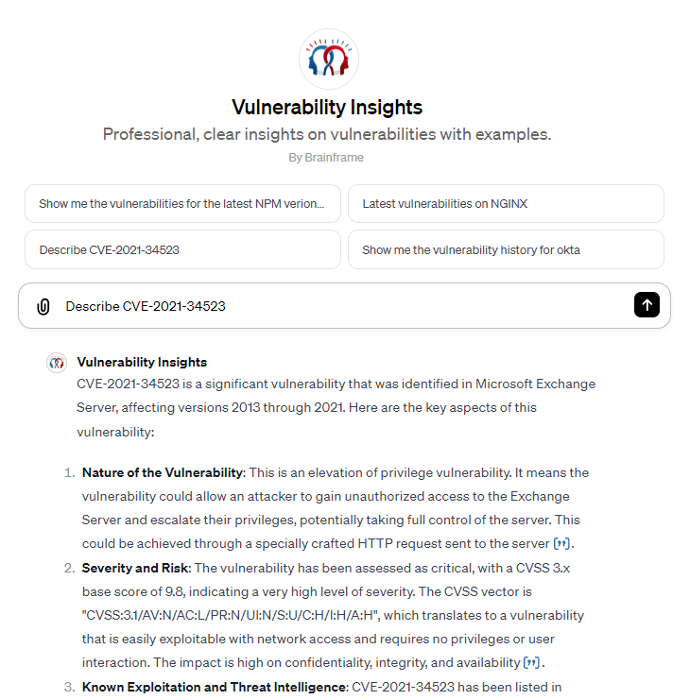
Vulnerability insights
Every day thousands of vulnerabilities are discovered in different software solution, libraries and online services that define your level of exposure. To help you gain time, we created a GPT* that lists you all details
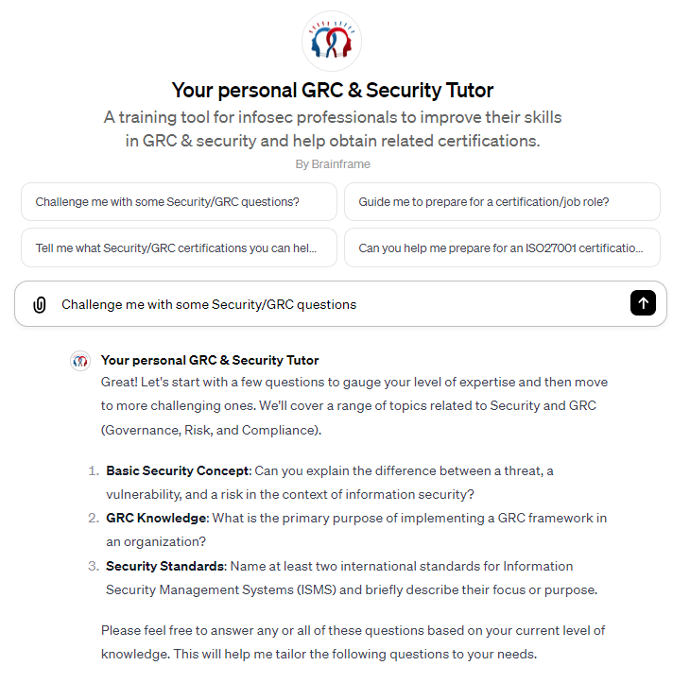
Your personal GRC tutor
You can't be perfect at everything from the start, especially not in the vast domain of GRC. This is why our tutor is there to help you improve your skills to help obtain related certifications. We highly recommend using this GPT* using your mobile device and use the conversation mode, so you can really be challenged in line with your expertise and in the domain of your choosing
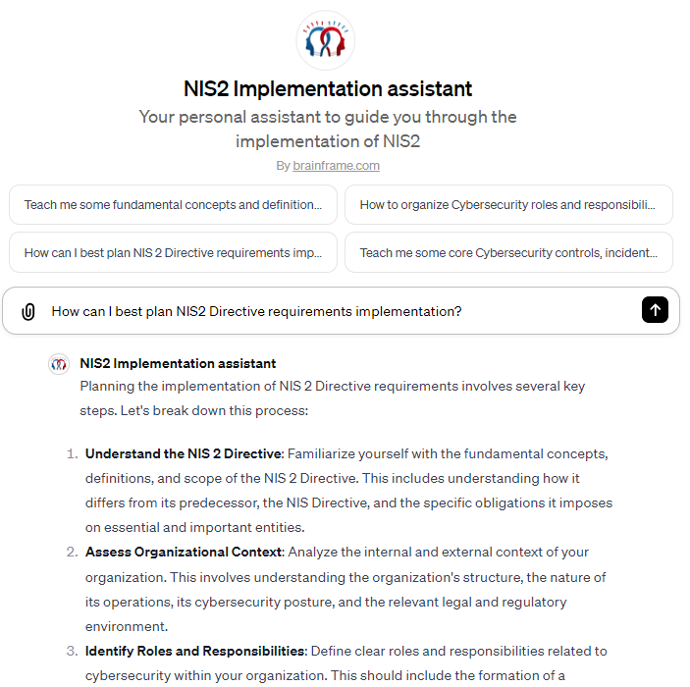
NIS2 Scope & Implementation assistant
Your personal assistant to guide you through the implementation of NIS2. Ask clarifications for specific concepts, requirements and best practices to help you efficiently implement the requirements of the directive
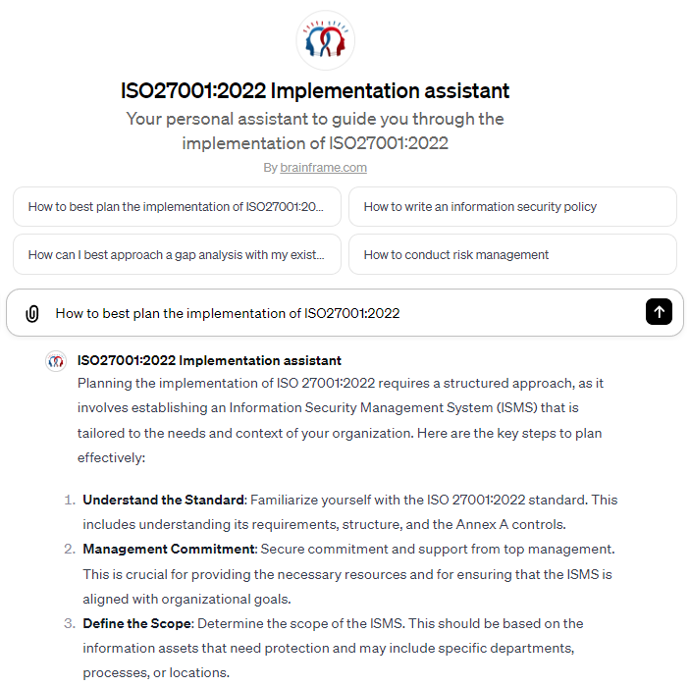
ISO27001:2022 Implementation assistant
Your personal assistant to guide you through the implementation of ISO27001:2022. Ask clarifications for specific concepts, requirements and best practices to help you efficiently implement the requirements of the standard
Brainframe ChatGPT plugin - ISO27001 Implementation assistant
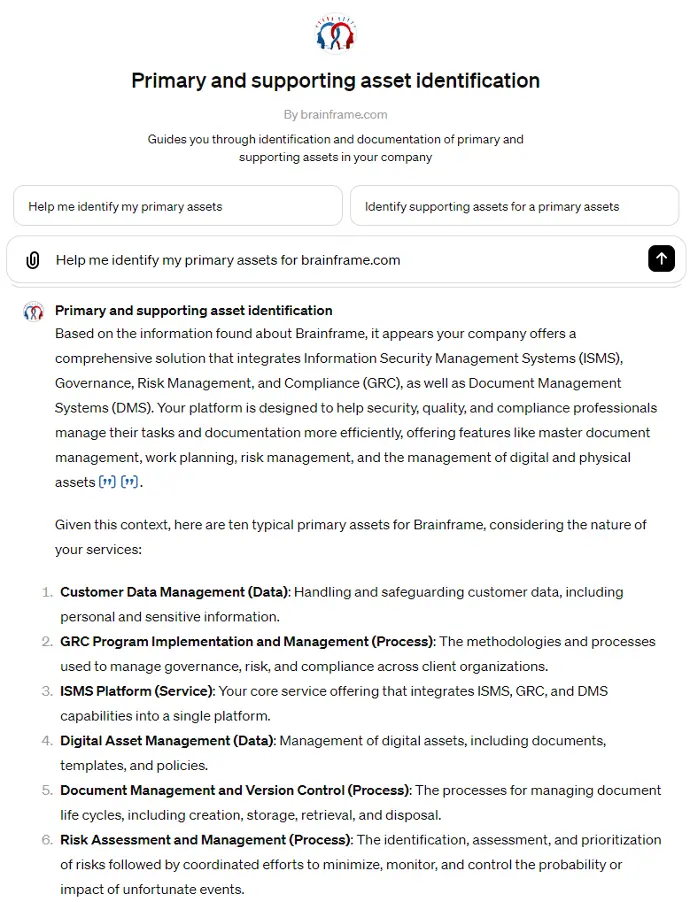
Primary & supporting asset identification
Get guidance during the identification of your primary and supporting assets
Brainframe ChatGPT plugin - Primary and supporting asset identification
Open source
Ready to use policies & procedures
A set of policies, standards and control procedures with mapping to ISO27001, GDPR, HIPAA, NIST CSF, PCI DSS, SOC2, FedRAMP, CIS Controls, and more.
These policies and procedures can be provided separately as part of your Brainframe instance, with a full integration into all our modules.
Center for Cybersecurity Belgium policy templates
A set of useful company policies provided by the Center of Cybersecurity Belgium (CCB). These reference documents are templates of Policies, instructions, inventories, lists, etc. and conform with the CyberFundamentals Assurance Level “Basic”.
Their objective is to allow you to quickly and easily implement a cybersecurity policy in your company.
Each model can be freely adapted, completed and customized according to your needs.

Software/Tools
Cyber security does not always need to be very expensive. Below is a curated list of open source or broad free usage tools you can use to improve your cyber posture
Network security & monitoring
- Wireshark: A network protocol analyser used for network troubleshooting, analysis, and communication protocol development.
- Snort: A network intrusion detection system (NIDS) capable of performing real-time traffic analysis and packet logging.
- Bro/Zeek: A powerful network analysis framework that focuses on security
- OpenNMS: An enterprise-grade network management application platform.
- Nmap: A network scanner used for network discovery and security auditing
- Nagios: A monitoring system that enables organizations to identify and resolve IT infrastructure problems.
- Pfsense: Probably the best and most flexible open source firewall around
- PacketFence: Free and open source network access control (NAC) solution with many integrated features (captive-portal for registration and remediation, central wired/wireless and VPN management, insustry-leading BYOD capabilities, 802.1x and RBAC support, anomaly detection with layer-2 isolation, ...)
- OpenSense: From Virtual Private Networking to Intrusion Detection, Best in class, FREE Open Source Project.
Endpoint protection
- Avast: Known for its solid protection against viruses and malware, including several features typically found in paid software. It includes a basic password manager, network security inspector, and even a hardened browser.
- Malwarebytes: A very nice and complete malware solution that is free for personal use
- AVG Antivirus: Now owned by Avast, offers similar protection to Avast. It's well-regarded for its effective detection of malicious software, user-friendly interface, and minimal impact on system performance.
- Bitdefender: Bitdefender is praised for its sleek design and minimalistic approach to antivirus protection.
- Kaspersky: Kaspersky's free version provides top-rated malware protection along with extra features like a VPN and password manager
- ClamAV: An antivirus engine designed for detecting Trojans, viruses, malware, and other malicious threats on mail gateways.
- OSSEC: An open-source, host-based intrusion detection system (HIDS) that performs log analysis, file integrity checking, policy monitoring, rootkit detection, and real-time alerting.
- Suricata: A high-performance network IDS, IPS, and network security monitoring engine.
- Wazuh: A security monitoring tool that provides host-based intrusion detection.
- chkrootkit: A tool to locally check for signs of a rootkit.
- Rkhunter: A Unix-based tool for scanning backdoors, rootkits, and local exploits.
- virustotal: Website to quickly scan any file/url for viruses/malware using many different anti-virus solutions
- Lookyloo: Check and review URLs and website and visualize their behaviour.
Email security
- GoPhish - A powerful phishing framework that makes it easy to test your organization's exposure to phishing
- SpamAssassin: A widely used tool for filtering and identifying spam. It uses a variety of spam detection techniques including DNS-based and fuzzy-checksum-based spam detection, Bayesian filtering, external programs, blacklists, and online databases.
- DKIM - Not really a tool, but so essential and free to implement
- DMARC - Similar to DKIM, not a tool but essential
- Pandora - quick, private and simple suspicious document analysis. (you can also just forward a mail to, [email protected] and receive a full analysis)
Source code analysis (SAST/SCA/Mobile)
- Snyk: Scan your own code and 3rd party code as well as your infrastructure code for vulnerabilities
- SonarQube: A widely used tool for continuous inspection of code quality. It performs automatic reviews to detect bugs, code smells, and security vulnerabilities.
- Brakeman: a static analysis tool specifically designed for Ruby on Rails applications. It scans Rails applications for security vulnerabilities.
- Bandit: A tool designed to find common security issues in Python code. It processes each file, builds an AST from it, and runs appropriate plugins against the AST nodes.
- FindSecBugs: A security-specific plugin for SpotBugs (formerly FindBugs), which is used for Java programs. It can identify security flaws in Java applications.
- ESLint: Statically analyzes your code to quickly find problems. It is built into most text editors and you can run ESLint as part of your continuous integration pipeline.
- OWASP Dependency-Check: Dependency-Check is a Software Composition Analysis (SCA) tool that attempts to detect publicly disclosed vulnerabilities contained within a project’s dependencies. It does this by determining if there is a Common Platform Enumeration (CPE) identifier for a given dependency. If found, it will generate a report linking to the associated CVE entries.
- Retire.js: Focused on JavaScript, Retire.js identifies the use of JavaScript libraries with known vulnerabilities.
- OSS Index: A free service by Sonatype, which provides information about known vulnerabilities in open-source software components.
Web application security, system/cloud security and vulnerability management
- OWASP ZAP: A penetration testing tool for finding vulnerabilities in web applications.
- SQLMap: An automated tool for SQL injection and database takeover.
- Nikto: A web server scanner which performs comprehensive tests against web servers.
- Arachni: A feature-full, modular, high-performance Ruby framework aimed at web application security testing.
- w3af: A web application attack and audit framework for web application security testing.
- OpenVAS: A framework of several services and tools offering vulnerability scanning and management.
- MobSF - Mobile Security Framework (MobSF) is a security research platform for mobile applications in Android, iOS and Windows Mobile. MobSF can be used for a variety of use cases such as mobile application security, penetration testing, malware analysis, and privacy analysis
- Nessus Essentials: A widely used vulnerability scanner with high-speed discovery, configuration auditing, and sensitive data discovery
- Burp Suite Free Edition: An integrated platform for performing security testing of web applications.
- Metasploit Framework: A tool for developing and executing exploit code against a remote target machine.
- PwnDoc - A pentest reporting application making it simple and easy to write your findings and generate a customizable Docx report
- Lynis: Open-source security auditing tool to do automated security auditing, compliance testing, vulnerability detection, configuration and asset management, software patch management, system hardening, ...
- CloudGrappler: Open-source tool detects activity in cloud environments. CloudGrappler is a purpose-built tool designed for effortless querying of high-fidelity and single-event detections related to well-known threat actors in popular cloud environments such as AWS and Azure
- CVE Prioritizer: CVE_Prioritizer is a powerful tool that helps you prioritize vulnerability patching by combining CVSS, EPSS, and CISA's Known Exploited Vulnerabilities. It provides valuable insights into the likelihood of exploitation and the potential impact of vulnerabilities on your information system.
- Faction: PenTesting Report Generation and Collaboration Framework
- Trufflehog: TruffleHog is an open-source scanner that identifies and addresses exposed secrets throughout your entire technology stack.
- ScoutSuite: Scout Suite is an open source multi-cloud security-auditing tool, which enables security posture assessment of cloud environments
- Harden 365: Harden365 is an Open Source security tool that can be used to hardening Microsoft 365 tenant with CIS and Microsoft recommendations. The Harden community is an association law 1901. It aims to help companies, especially an SMB or TPE, to improve the security of its information system.
- PurpleOps: Purple Team Management Platform. Create assessments aligned with MITRE ATT&CK, leveraging data from sources like Atomic Red Team and SIGMA. Centralise blue and red team data for evaluation. Iterate and improve organisational cybersecurity capabilities.
DNS security
- Subdominator: CLI tool for detecting subdomain takeovers
- DNS-Dumpster: Free domain research tool that can discover hosts related to a domain. Finding visible hosts from the attackers perspective is an important part of the security assessment process.
- Whois record: Free lookup of ownership, registration and contact information about a given domain name
SSL Certificates
- SSL-Labs: Free online service performs a deep analysis of the configuration of any SSL web server on the public Internet
Hardware and firmware security
- EMBA: The security analyzer for firmware of embedded devices (Enhanced firmware extraction process, UEFI analysis, Firmware diffing mechanisms, user mode emulation, system emulation, ...)
Identity management
- Keycloak: Open Source Identity and Access Management. Add authentication to applications and secure services with minimum effort. No need to deal with storing users or authenticating users. Keycloak provides user federation, strong authentication, user management, fine-grained authorization, and more.
- Adalanche: Adalanche gives instant results, showing you what permissions users and groups have in an Active Directory. It is useful for visualizing and exploring who can take over accounts, machines or the entire domain, and can be used to find and show misconfigurations.
- SOAPHound: Open-source tool to collect Active Directory data via ADWS. SOAPHound is an alternative to a number of open source security tools which are commonly used to extract Active Directory data via LDAP protocol. SOAPHound is able to extract the same information without directly communicating to the LDAP server. Instead, LDAP queries are wrapped within a series of SOAP messages, which are sent to the ADWS server using NET TCP Binding communication channel. Following, ADWS server unwraps the LDAP queries and forwards them to the LDAP server running on the same Domain Controller. As a result, LDAP traffic is not sent via the wire and therefore is not easily detected by common monitoring tools.
- Pink castle: Ping Castle is a tool designed to assess quickly the Active Directory security level with a methodology based on risk assessment and a maturity framework.
- Bastillion: Bastillion is a web-based SSH console that centrally manages administrative access to systems. Web-based administration is combined with management and distribution of user's public SSH keys. Key management and administration is based on profiles assigned to defined users. Administrators can login using two-factor authentication with Authy or Google Authenticator. From there they can manage their public SSH keys or connect to their systems through a web-shell. Commands can be shared across shells to make patching easier and eliminate redundant command execution. Bastillion layers TLS/SSL on top of SSH and acts as a bastion host for administration
- Harden AD: Hardening Active directory tool
- Pingcaslte: Gets Active Directory Security at 80% in 20% of the time
Security Information and Event Management (SIEM) and Log management
- Wazuh: Unified XDR and SIEM protection for endpoints and cloud workloads
- ELK Stack: A collection of three open-source tools (Elasticsearch, Logstash, Kibana) for searching, analyzing, and visualizing data in real-time.
- OSSIM: A SIEM software that provides threat detection, incident response, and compliance management.
- Graylog: A log management and analysis tool for security and debugging.
- Apache Metron: Integrates a variety of open source big data technologies to offer a centralized tool for security monitoring and analysis.
- MasterParser: MasterParser stands as a robust Digital Forensics and Incident Response tool meticulously crafted for the analysis of Linux logs within the var/log directory. Specifically designed to expedite the investigative process for security incidents on Linux systems, MasterParser adeptly scans supported logs, such as auth.log for example, extract critical details including SSH logins, user creations, event names, IP addresses and much more.
- Tracecat: Open source Tines / Splunk SOAR alternative
- SELKS: Free and open source IDS/IPS/Network Security Monitoring platform
Password managers
- Passbolt - Password manager built for organizations that take their security and privacy seriously
- KeePass: A password manager helping you to manage your passwords securely.
- Bitwarden: a free and open-source password management service that stores sensitive information in an encrypted vault. It is known for its ease of use and cross-platform compatibility.
Incident response, Risk assessment, Threat intelligence, Posture management
- AWS Kill switch - a Lambda function (and proof of concept client) that an organization can implement in a dedicated "Security" account to give their security engineers the ability to quickly deploy restrictions during a security incident
- TheHive - Open source and free Security Incident Response Platform designed to make life easier for SOCs, CSIRTs, CERTs and any information security practitioner dealing with security incidents that need to be investigated and acted upon swiftly
- Cortex - Tries to solve a common problem frequently encountered by SOCs, CSIRTs and security researchers in the course of threat intelligence, digital forensics and incident response: how to analyze observables they have collected, at scale, by querying a single tool instead of several
- MISP: A platform for sharing threat intelligence and malware information.
- Monarc: A tool and a method allowing an optimised, precise and repeatable risk assessment.
- Yeti: Aims to bridge the gap between CTI and DFIR practitioners by providing a Forensics Intelligence platform and pipeline for DFIR teams
- Web-Check: Comprehensive, on-demand open source intelligence for any website. Web Check offers thorough open-source intelligence and enables users to understand a website’s infrastructure and security posture, equipping them with the knowledge to understand, optimize, and secure their online presence.
- Shodan: Shodan is the world's first search engine for Internet-connected devices. Discover how Internet intelligence can help you make better decisions
- CrowdSec: Curated Threat Intelligence, Powered by the Crowd
Secure file sharing
- LinShare: Specially designed to secure paperless file sharings within companies that put privacy and traceability in the heart of their problems of exchange, LinShare provides a simple solution completely intuitive. Linshare allows employees to "upload files into their space", "share files with internal or external collaborators" and "offers several features to securely exchange"
Automation
- Shuffle: Shuffle is an open source automation platform, built for and by the security professionals. Security operations is complex, but it doesn't have to be. Built to work well with MSSP's and other service providers in mind.
Asset management
- GLPI - GLPI stands for Gestionnaire Libre de Parc Informatique is a Free Asset and IT Management Software package, that provides ITIL Service Desk features, licenses tracking and software auditing.
Various
- ProxMox: Proxmox delivers powerful, enterprise-grade solutions with full access to all functionality for everyone - highly reliable and secure. The software-defined and open platforms are easy to deploy, manage and budget for. They offer a solution for Virtualization, backups and email security
Other more generic open source promoted by EU
Feel free to suggest things we can list on our community page that will help people improve their security: