Why Post-Quantum Cryptography Matters Now
Quantum computing is no longer science fiction. It’s quietly moving from theory to practical threat. While mainstream quantum computers still have limitations, nation-state actors and advanced adversaries are already preparing for the shift. That’s where post-quantum cryptography (PQC) comes in—not as hype, but as a strategic necessity.
One of the key risks comes from the “harvest now, decrypt later” tactic. Attackers don’t need quantum computers today to start collecting your encrypted data. If your organization deals with sensitive long-lived data, there’s a real risk that this data will be decrypted once quantum capabilities mature.
Here’s the core equation every cybersecurity leader should keep in mind:
Time to implement new standard + Data lifetime value < Time until quantum attacks become feasible
This means even if quantum attacks are still 10–15 years away, the planning and migration need to start now.
Why this matters:
- Encrypted data has a shelf life: Financial records, health data, intellectual property can still be damaging years later.
- Implementing PQC takes time: From identifying what needs protection to updating infrastructure and training staff.
- Regulators are starting to take notice: NIST has selected standard candidates, and organizations that wait too long risk being non-compliant.
In short, post-quantum cryptography is about being realistic. The clock is ticking, and security teams that prepare early will be in a much stronger position to handle the transition smoothly and securely.
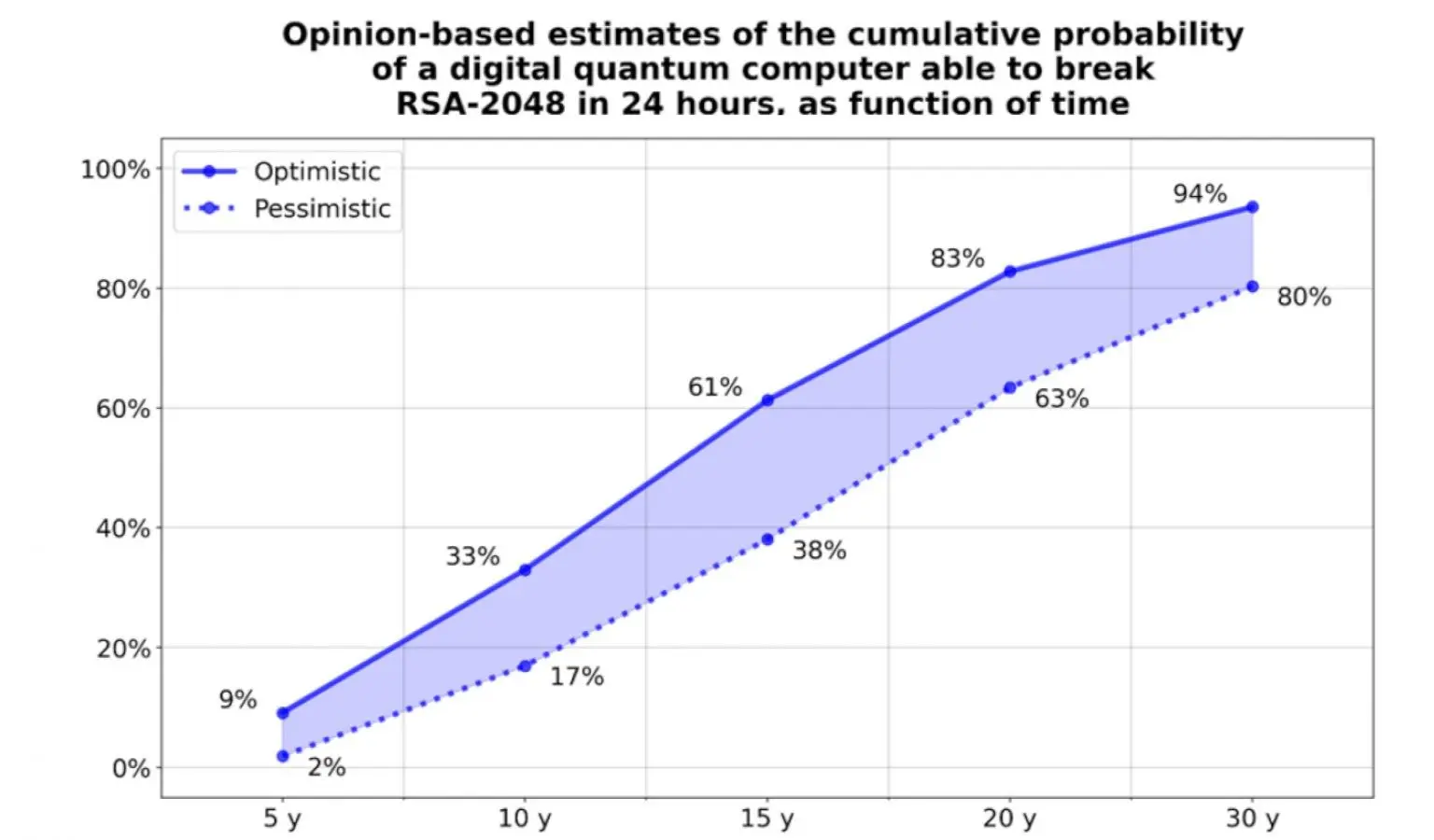
How Soon Is Quantum? This Chart Says: Sooner Than You Think
The graph above shows expert estimates on the probability of a quantum computer breaking RSA-2048 encryption within 24 hours, over time. It highlights both optimistic and pessimistic views, based on surveys of quantum computing specialists.
Key takeaways:
- Within 10 years, there's a 33% chance (optimistic view) that RSA-2048 could be broken in under a day.
- By 20 years, the probability climbs to 83%, and even the conservative estimate hits 63%.
- At the 30-year mark, almost everyone agrees: there's an 80–94% chance we’ll have quantum systems powerful enough to break today’s most widely used encryption.
This isn’t just theoretical. If your data needs to remain confidential for 10+ years, the quantum clock is already ticking. You don’t want to be the last one to migrate when attackers are already harvesting encrypted data to crack later.
Taking Inventory: Know What You Need to Protect
Before you can migrate to post-quantum cryptography, you need to know where cryptography lives in your environment. Spoiler: it's not just in your VPN or email. Cryptographic functions are embedded in more places than most teams realize.
A proper inventory is a foundation for decision-making.
Start with what you can see:
- Public-facing endpoints: Web servers using TLS, remote access tools, APIs.
- Internal services: Encrypted databases, authentication systems, backup tools.
- Certificates and keys: PKI assets, code signing certs, mobile provisioning profiles.
Don’t ignore the hidden layers:
- Legacy systems: Older apps with hardcoded keys or outdated libraries.
- Third-party tools: Vendors may use cryptography you don’t control.
- Containers and cloud functions: Short-lived environments still encrypt data.
This step often reveals surprises. Maybe your build pipeline signs artifacts with a certificate that hasn’t been rotated in years. Maybe a forgotten admin tool still relies on deprecated crypto protocols. Either way, you can’t protect what you haven’t mapped.
Automation helps, especially at scale. Consider using:
- Cryptographic discovery tools that scan binaries, traffic, and systems.
- CMDB integrations to tie crypto use to assets and owners.
- Scripts to extract and catalog TLS endpoints, SSH keys, and cert chains.
The end goal? A living cryptographic inventory. It should tell you what algorithms are in use, where they’re used, and who owns each asset. Without this, a PQC transition becomes guesswork, and that’s not a strategy.
Prioritize What Really Matters
Once you have a handle on your cryptographic assets, the next step is to avoid treating them all the same. Not every encrypted connection or key is equally critical. Some protect low-risk data, others are tied to your crown jewels.
Prioritization ensures you're not wasting resources patching things that don't need fixing yet, while high-impact systems sit exposed.
Start by classifying your data:
- Is it sensitive? Think customer data, trade secrets, medical records.
- How long must it remain confidential? A 20-year data retention policy raises the stakes.
- Would exposure cause regulatory issues or reputational damage?
Link data to processes:
- Does it affect critical operations? Look at payroll, authentication, code deployment.
- Is it customer-facing? Anything exposed to the public usually needs higher priority.
Add context to your crypto assets:
- Encryption on a test server probably isn’t a priority.
- TLS on your production e-commerce platform absolutely is.
Once you’ve mapped your data and business processes to cryptographic usage, the next step is clear: create a tiered remediation plan. For example:
- Tier 1: Must be upgraded ASAP (customer auth, core databases, backups).
- Tier 2: Important but can wait (internal tools, less-sensitive data).
- Tier 3: Monitor and revisit later (sandbox systems, low-risk services).
Prioritization avoids panic and keeps your post-quantum effort grounded in reality. You don’t need to boil the ocean—just focus on what can burn you first.
Plan the Migration: PQC Is Not Plug-and-Play
You can’t just swap out an algorithm like you’re updating a browser plugin. Post-quantum migration takes time, testing, and coordination across teams. The deeper crypto is buried in your stack, the harder the replacement gets.
A smart migration plan starts with what you already know from your inventory and prioritization efforts.
Break the process into phases:
- Assessment: Identify what can be upgraded easily and what needs major rework.
- Pilot: Test PQC in isolated environments, especially in dev and staging.
- Rollout: Gradually replace classical algorithms in production systems.
Expect growing pains:
- Post-quantum algorithms are heavier. Larger keys and signatures can affect performance.
- Not all vendors are ready. Hardware, cloud providers, and APIs may lag behind.
- Interoperability issues will crop up—especially in hybrid environments.
NIST has already selected four standard post-quantum algorithms, including CRYSTALS-Kyber for key encapsulation and CRYSTALS-Dilithium for digital signatures. These were chosen for their balance of performance, security, and broad applicability, but real-world implementations will often use hybrid approaches combining classical and quantum-safe crypto. This keeps you compatible while adding future-proofing.
You’ll also need to:
- Update protocols (TLS, IPsec, SSH).
- Replace libraries (OpenSSL, BoringSSL, etc.).
- Rethink key management—some algorithms don’t work well with traditional methods.
And don't forget compliance. Regulators will start asking for post-quantum readiness soon. Including it in your roadmap now will save you from a last-minute scramble later.
Bottom line: migration is a project, not a patch. Start small, plan smart, and keep moving.
Governance, Compliance & Team Alignment
If only the security team knows what’s happening, you’re setting yourself up for blockers, delays, and misalignment.
Make it a cross-functional initiative. Everyone from compliance officers to DevOps needs to understand what’s changing and why.
Fold PQC into your existing governance:
- Update your risk register to include quantum threats.
- Tag cryptographic assets in your asset management system as quantum-vulnerable or quantum-safe.
- Include PQC in audits and internal reviews so stakeholders see it as part of ongoing resilience.
Align with regulatory frameworks:
- NIST SP 800-208 offers transition guidance—worth integrating into internal policies.
- ISO/IEC 18033 and ISO/IEC 23837 (in development) cover quantum-safe encryption standards.
- Industry regulators are watching, especially in finance, healthcare, and defense.
Get your people on board:
- Train engineers and architects on post-quantum algorithms and how they differ from traditional ones.
- Brief compliance and legal teams so they’re ready to respond to audits or client questions.
- Communicate progress up the chain—boards will care once they understand the risk.
You don’t need a separate PQC task force, but you do need clear ownership:
- Who's responsible for updating crypto libraries?
- Who tracks vendor readiness?
- Who signs off on key migrations?
Treat PQC as a governance topic, not just a technical one. That’s how it gains visibility—and budget.
Looking Ahead: Building Crypto-Agility
Quantum-safe algorithms are coming, but they won’t be the last change you’ll need to make. The real goal isn’t just migration. It’s crypto-agility: the ability to upgrade cryptographic mechanisms without rewriting half your infrastructure.
Design with change in mind:
- Abstract your crypto functions so algorithms can be swapped without breaking workflows.
- Use centralized key management instead of embedding keys in code or configs.
- Avoid proprietary crypto unless you’re absolutely sure you can control and update it.
The next time algorithms are broken—or new standards emerge—you want to be ready with minimal friction.
Track the standards that matter:
- NIST’s post-quantum recommendations will evolve as more testing and implementation feedback comes in.
- ETSI and ISO are also shaping international guidelines. Keeping tabs helps you stay ahead of compliance curveballs.
- Vendor roadmaps are worth monitoring. Ask your suppliers when and how they plan to support PQC.
Keep crypto under regular review:
- Run cryptographic assessments annually, not just after incidents.
- Set KPIs: % of systems migrated to PQC, # of quantum-vulnerable endpoints, time to patch crypto libraries.
- Join industry forums or working groups to stay informed and exchange knowledge.
If your systems are flexible, and your teams are informed, you won’t have to panic the next time crypto needs an overhaul. You’ll already have the structure in place.