Let's ask the right questions
Managing cybersecurity and compliance can be done in many different ways, and all depends on the size and complexity of your company. There are many great cybersecurity frameworks that can be implemented like NIST, ISO27001, CIS, CCM, COBIT, CSF, BSI, ... which all take a structured approach and help you ensure all is covered eventually.
But no matter how you are organized or where you put priority, the key questions regarding security and compliance always remain more or less the same.
This article aims to give some simple questions that top management should be asking their teams to understand how prepared and resilient they really are.
People management
- Do you conduct background checks before hiring people?
- Do you properly onboard people so they know what they need to do and how?
- Do you know who is no longer happy to work for your company, and risks to steal or simply leave with important knowledge?
- Do your people have possibilities to grow inside your company, avoiding them to go look elsewhere?
- Does staff have an easy way to escalate issues through another way than their manager?
- Do you have an anonymous notification mechanism in place for security issues/incidents?
- Are roles and responsibilities properly documented?
- Have you included "people" in your business continuity plan?
- Are all key business systems accessible in case some staff members are not available/left?
- Is there a clear support from top management for your security program?
- Does everyone understand the mission, vision and purpose of the company, and how your security program fits into it?
- Do you know your company's key stakeholders and their expectations?
- Do you have a governance board in place where top management regularly reviews key security and compliance elements?
- Do you know who your customers really are?
- Have you checked that your customers do not have a criminal background or history of malicious practices?
- Does your staff know that in case of a security incident, they are not allowed to communicate with the outside world unless approved?
- Do you implement segregation of duties?
Password & access management
- Do you force your staff to use a password manager?
- Do you know and document who has access to what, (since) when and why?
- Do you regularly review access privileges?
- Are people reusing (personal) passwords?
- Have you checked if company passwords are publicly leaked (haveibeenpwnd.com)
- Are you implementing the principle of least privilege/need to know?
- Are internal changes of job role resulting in a review of access privileges?
- Do you have a single sign on solution in place so you can quickly remove all access when needed?
- Do you enforce multi factor authentication everywhere where possible?
- Do you train your staff or enforce good password practices?
- Do you allow users to share credentials as group accounts, and if so, how will you investigate who did what when it is needed?
- Do you rotate passwords (including those for WIFI access)?
- Are the encryption keys for key applications properly backed up and always available?
Cloud security
- What would happen if your cloud data (G Suite, Microsoft 365, ...) got stolen, locked or corrupted due to ransomware or simply (accidentally) removed?
- How much time would it take for you to restore it so business is no longer blocked?
- Are your Amazon Web Services or Azure resources properly protected?
- Are you profiting from all security services already included in your cloud services?
- Are your critical business services protected against denial of service attacks?
- Have you defined rules on who can do what in your cloud?
- Do you have protections/notifications in place for out of control costs?
- Do you verify your service provider's security and compliance practices before using them?
- Are you monitoring events reported by your cloud solution?
- Do you have all cloud logging features enabled to allow proper forensics when needed?
- Are your cloud data storage interfaces not publicly accessible (s3 permissions, ...)?
- Do you have a backup of all your data (mails, files, source code, credentials, ...)?
Communication security
- What could a competitor do with the information in your mailbox?
- Do you prevent personal data, passwords and other sensitive data to be sent per mail?
- Are your current communication flows compliant with privacy regulation?
- Do you forbid using insecure communication technologies (eg FTP)?
- Do you allow company emails on unprotected employee owned devices?
- What is your retention policy on personal data?
- Can the data you send in local network or on the internet be intercepted/altered in transit? (employees, ISP, attacker, ...)
- Are you using up to date encryption methods?
- Is staff aware that "free" WIFI in hotels or pubs are a huge security risk?
- Do you know who is connected to your verify wireless devices?
- Are all wireless access points yours and under your control?
- Is your staff aware about the risks of free/public WIFI?
Legal and compliance
- Do you have a register of all regulatory requirement and standards you need to comply with?
- Do you have a mapping of these requirements to what you actually do?
- Do you have written down how you want your staff to behave (policies & procedures)?
- Does your staff know and understand the rules you want them to respect?
- Do you measure the effectiveness of your rules?
- Do you have social media guidelines in place?
- Have you defined a general code of conduct?
- Is it clear what happens when rules are not respected?
- Are you able to give a clear reply to partners (e.g. customers, suppliers, investors, ...) what you actually enforce internally, or is it more an unwritten rule?
- Do you document and enforce in the form of policies and procedures with your partners (e.g. suppliers, consultants) how you want them to behave?
- Do you have an information security management system that documents all your security/compliance efforts?
- How is our intellectual property protected (patents, trademarks, ...)
Endpoint security
- Are the computers and mobile devices in use by your staff properly protected (encryption, passwords, antivirus)?
- Are you informed when one of your endpoints gets infected (or when it is attempted).
- Can you isolate this device to prevent spreading to other devices?
- Do you have a method to analyse and collect forensic proof after an incident?
- Is the data on centrally stored, or will your data also be lost when devices compromised?
- Does your staff use illegal software (with most probably some backdoors)?
- Are your people aware they should report weird behaviour, and how?
- Are your devices automatically locked?
- Do you ensure local users don't have admin privileges on their own devices?
- Do you have a software approval list or blacklist?
- Do you manage which browser extensions are/can be installed?
- Do you have a way to remotely wipe a device in case of theft?
Data management
- Is your corporate data spread over many different systems and workstations or centrally stored and protected?
- How does staff access your corporate data (remotely)?
- Do you have a data processing register defining what data you process, what it is used for, and on which system?
- Have you classified different types of information, so you know what is more important to protect than other things?
- Do your web servers have files on them that should not be publicly accessible?
- Do you have clear rules on how private devices can be used for company data?
- Have you mapped the different existing information flows?
- Do you know what are the RTO and RPO for your data recovery procedures?
- What information is publicly available on your company using OSINT?
Attack mitigation
- Are you tracking (unauthorized, unsuccessful) access to your systems?
- Is there any activity information available on the dark net about your company
- Are you detecting which countries are connecting to your systems, and is it normal?
- Can you automatically block common attacks?
- Are devices properly hardened for remote work?
- Do you have a documented security baseline to know what is normal and what is not?
- Do you know when your website starts loading scripts from other sources than intended?
- Are you able to quickly block specific users or malicious actor IPs?
- Are you making backups of the right things?
- Are those backups available, and working?
- Do you have honeypots or other "distractions" in place to slow down attackers?
- Are the encryption methods used to protect our data up to date and efficient?
- Is our data encrypted at rest?
- Who has access to our sensitive production data?
Security awareness training
- Has all staff received appropriate and easy to understand security and compliance awareness training?
- Have you documented who received the training and who not?
- Are people aware of social engineering and phishing email risks?
- Does your staff know how to report security incidents and why a timely way of doing so is important?
- Does your staff consider security as a IT responsibility, or have they been trained that this is a shared responsibility?
- Do you regularly repeat your trainings?
- Do you evaluate your trainings?
Vulnerability management
- Are you following/being notified when new zero-day vulnerabilities are discovered?
- Is your source code automatically scanned for vulnerabilities?
- Do you implement code review to avoid bad/vulnerable coding?
- Do all your systems get regular security updates?
- Do you have a responsible disclosure mechanism in place allowing anyone to inform you about security issues?
- Do you proactively stay on the latest versions of software, infrastructure and development frameworks to ensure you are using tools that are maintained
Securing IT infrastructure
- Are your internal systems properly secured?
- Are you using infrastructure as a code to easily reproduce in case needed?
- Do you use immutable container builds (eg docker) for easy to reproduce server configurations?
- Do you have isolated test environments (development, testing, staging, production)
- Do you know what are the RTO and RPO for your infrastructure recovery procedures?
- Will you be notified if there is suspicious activity on your systems?
- Do you have a old hardware replacement cycle in place?
- Are there unidentified devices plugged in your network/servers?
- Do you have an inventory of all your devices and their ownership?
- What's the impact on your business if any of of your infrastructure components go down?
- Are changes to infrastructure documented and risk evaluated prior to implementation?
Security audits
- Do you do security audits for the checkbox or for continuous improvement?
- Have you had an independent review of the actual security level of your core systems & applications?
- How does a real hacker exploit my business?
- Do you conduct internal audits onto check your actual level of security?
- Do you document finding that should be fixed (even if there is not now)?
Secure software development
- Are all changes to code documented and risks of change evaluated prior to change?
- Are your application protected against the OWASP top 10 ?
- Injection
- Broken authentication
- Sensitive data exposure
- XML External Entities
- Broken access control
- Security misconfiguration
- Cross-site scripting
- Insecure deserialization of user input
- Components with known vulnerabilities
- Insufficient logging/monitoring
- Is your code regularly scanned for vulnerabilities?
- Do you have a regular backup of your source code repository?
- Are changes to code tracked to individuals as part of a source code repository?
- Is source code review enforced prior to going to production?
- Are you running automated tests to avoid new code breaking existing functionality?
- Are you scanning your own source code using static code analysis solutions to discover security issues early during development?
- Are you scanning 3rd party libraries and dependencies of your code on vulnerabilities?
- Are you sure that you do not use any 3rd party libraries and dependencies code which when discovered forces you to make your own code public?
Zero trust
- Have you identified your attack/protect surface?
- How easy is it for an attacker to do lateral movement within your systems once they get a first step in?
- Have you build up your architecture in such a way that all resources require authentication and no system "trusts" the other by default?
Security logging & monitoring
- Do you have a security information and event management (SIEM) in place where you centrally collect all events from different systems?
- Are you monitoring unsuccessful login attempts?
- Are you notified if your website suddenly loads resources from other websites to compromise your visitors?
- Do you have a security baseline?
- Is your infrastructure properly being monitored to detect inconsistencies?
- Are your logs immutable even for administrators?
- Is the time of your systems synchronised so that logs give a proper chronological view?
Supplier management
- Are all your suppliers documented?
- Do you have contracts in place with all your suppliers?
- What is the level of security you expect from your suppliers, and do you know/commit to it?
- Does your business stop if one of your suppliers can no longer deliver?
Data privacy compliance
- Do you have an internal data processing register?
- Have you identified the different types of data you process, and if any of them fall under the "sensitive data" category needing additional protection?
- Have you appointed an "impartial" data protection officer (DPO) with appropriate training?
- Are you and your staff aware about the data breach notification obligations and their deadlines?
- Are your services GDPR compliant?
- Are you properly handling data subject request and in a timely manner?
- Are you properly collecting data subject consents?
- Have you conducted data impact analysis?
- Are you sure that production data is not used in testing or development environment?
- Are all the cookies places on your websites covered by a legal basis?
- Do you have contacts in place with the supervisory authorities in case of a breach?
- Did you have an audit done on your data privacy compliance?
Physical security
- Are the keys/security badges to access our buildings documented and collected at end of contract?
- Do we have an alarm system in place for intrusion/fire detection that notifies someone who can react immediately at any time?
- Are your fire extinguishers regularly checked?
- Do we have evacuation procedures in place with clearly defined roles and responsibilities in case of an incident?
Management system
Then last, but not least is wetter you have a good management system in place where you can document and keep track of all these questions and the answers you came up with.
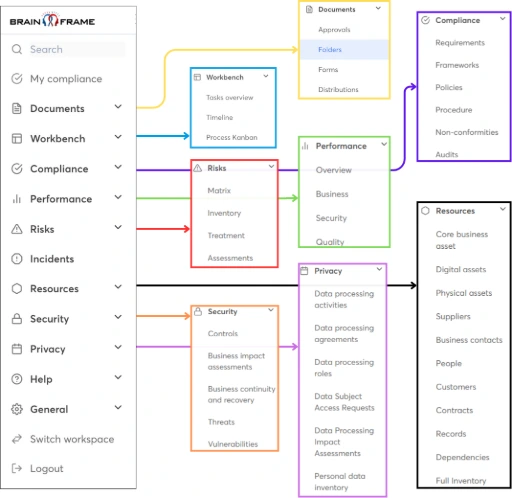
To do all of the above effectively, you cannot rely on Word and Excel, because you'll need many different tools to properly document and version everything, to communicate with your staff, to understand dependencies between assets and requirements, to do risk management and prioritisation, to track KPIs and progress, to store meeting notes, to do task planning and delegation, to build action plan roadmaps, to collect new incoming information from your staff and generally speaking, to effectively govern your company.
This is exactly why we made Brainframe.com, your all in one GRC/ISMS.
Start for free now!
Like with GDPR, don't wait until the last moment because this will only be more expensive and put unneeded stress on your teams!
Subscribe to our newsletter
By providing your email we'll send you updates on our service per email
(not more than one mail per week).