The NIST Cybersecurity Framework (CSF) is a voluntary framework that helps organizations manage cybersecurity risk. Developed by the National Institute of Standards and Technology (NIST), the NIST CSF provides a security framework of best practices and guidelines to help organizations of all sizes improve their cybersecurity posture. It offers a structured approach to managing several key aspects:
- Managing cybersecurity and cybersecurity risk.
- Enhancing cybersecurity governance.
Ultimately, the framework aims to strengthen an organization’s cybersecurity against evolving cybersecurity threats.
Overview of the NIST Cybersecurity Framework
What is the NIST CSF?
The NIST Cybersecurity Framework, often referred to as the NIST CSF, is a cybersecurity framework, one of the most widely adopted ones, designed to help organizations manage cybersecurity and cybersecurity risk. It is a flexible, repeatable, and cost-effective approach to managing cybersecurity, not a one-size-fits-all security standard. The framework is built upon industry best practices and existing security controls, allowing organizations to tailor its implementation to their specific needs and cybersecurity risk profile.
Importance of Cybersecurity Frameworks
Cybersecurity frameworks provide a structured and systematic approach to managing cybersecurity. Frameworks like the NIST CSF provide essential guidance for organizations of all sizes to enhance their cybersecurity posture. These frameworks promote a common language and understanding of cybersecurity risk, fostering collaboration and communication within the cyber domain. Employing a framework is vital in proactively mitigating cybersecurity threats, improving security posture, and reducing the impact of potential data breaches and cybersecurity events.
Key Components of the NIST Framework
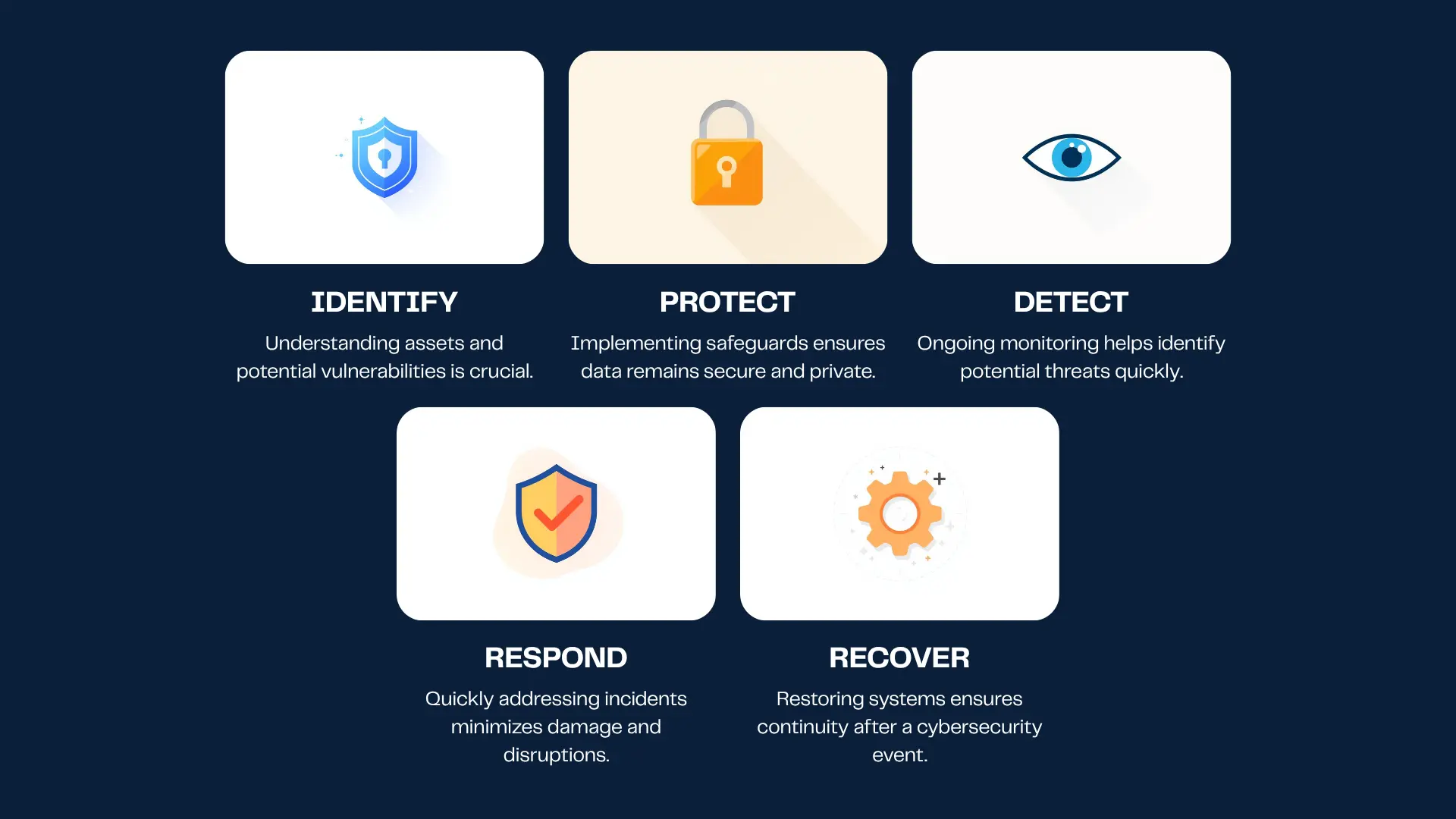
The NIST Cybersecurity Framework is structured around five core functions: Identify, Protect, Detect, Respond, and Recover. These functions work together to provide a comprehensive and dynamic cybersecurity strategy. The latest version of the CSF places even greater emphasis on cybersecurity governance and supply chain risk management.
| Function | Focus Areas |
|---|---|
| Identify | Asset management and risk assessment |
| Protect | Implementing security controls |
| Detect | Cybersecurity event detection and analysis |
| Respond | Incident response planning and execution |
| Recover | Restoring capabilities and services after a cybersecurity event |
Understanding the CSF 2.0
Overview of Version 2.0
The NIST CSF 2.0 represents a significant evolution in the cybersecurity framework landscape. This version 2.0 builds upon the solid foundation of the original framework, incorporating lessons learned and addressing emerging cybersecurity threats. The NIST CSF is designed to help organizations better manage cybersecurity and cybersecurity risk. It maintains the core principles of being voluntary, flexible, and technology-neutral, making it adaptable to diverse cybersecurity posture and cybersecurity governance needs across various sectors including critical infrastructure.
New Features and Enhancements
Version 2.0 of NIST introduces several key enhancements, primarily a renewed focus on cybersecurity governance and supply chain risk management. The updated framework also places greater emphasis on risk assessment and the integration of cybersecurity risk considerations into broader enterprise risk management strategies. New guidance is provided to help organizations better manage cybersecurity risk and ensure their cybersecurity practices are aligned with their overall business objectives. These improvements make the NIST CSF an even more powerful tool for strengthening an organization’s cybersecurity.
Comparing CSF 2.0 to Previous Versions
Comparing CSF 2.0 to its predecessor, several notable changes emerge. While the core functions of Identify, Protect, Detect, Respond, and Recover remain central, version 2.0 provides more detailed guidance and examples for each. The updated framework places a stronger emphasis on cybersecurity governance and supply chain risk management, recognizing the growing importance of these areas in today's complex cyber landscape. The NIST framework also features enhanced risk assessment methodologies to help organizations better manage cybersecurity.
Implementing the Framework
Steps to Implement the NIST CSF
Implementing the NIST CSF involves a systematic approach to managing cybersecurity, starting with a thorough risk assessment to understand your organization’s cybersecurity vulnerabilities and cybersecurity risk profile. Next, you should develop a plan to address identified gaps, prioritizing security controls based on your risk management strategy. It's important to tailor the security framework to your specific needs and resources. Continuously monitor and improve your cybersecurity posture over time, adapting to new cybersecurity threats and evolving business requirements. The NIST CSF is not a one-time project but an ongoing cybersecurity program.

Framework Core and Cybersecurity Activities
The NIST Cybersecurity Framework Core helps organizations create a robust cybersecurity strategy. It consists of five functions, each divided into categories and subcategories, providing a roadmap for improving critical infrastructure cybersecurity and enhancing data security. These functions guide organizations in performing specific cybersecurity activities.
| Function | Example Cybersecurity Activity |
|---|---|
| Identify | Asset Management |
| Detect | Vulnerability Scanning |
| Respond | Incident Response Planning |
| Recover | Data Breach Recovery |
The framework is designed to help organizations integrate these cybersecurity practices into their daily operations.
Managing Cybersecurity Risk with NIST Framework
The NIST Cybersecurity Framework is a powerful tool for managing cybersecurity risk and reducing the likelihood and impact of cybersecurity events. By using the NIST CSF, organizations can identify and prioritize cybersecurity risks, implement appropriate security controls, and monitor their cybersecurity posture. This proactive approach to managing cybersecurity helps mitigate cybersecurity threats, protect critical asset management, and maintain business continuity. Ultimately, the NIST framework provides a structured and repeatable process for helping organizations.
Framework for Improving Critical Infrastructure
Importance for Critical Infrastructure
The NIST Cybersecurity Framework is particularly crucial for critical infrastructure sectors, which are vital to the functioning of a nation. Improving critical infrastructure cybersecurity involves protecting systems and assets that are essential, and the framework offers a structured approach to managing cybersecurity and mitigating cybersecurity risk. By adopting the NIST CSF, these sectors can enhance their resilience against cybersecurity threats and ensure the continuity of essential services. The NIST framework provides a security framework tailored to these complex environments.
Security Controls in Critical Systems
Implementing effective security controls within critical infrastructure systems is essential for improving critical infrastructure cybersecurity. The NIST Cybersecurity Framework provides guidance on selecting and implementing appropriate security controls based on risk assessment and the specific needs of the organization’s cybersecurity. These controls may include access controls, encryption, intrusion detection systems, and incident response plans. The NIST SP 800-53 further details the implementation of these security controls, enhancing data security and overall system resilience against cybersecurity threats.
Guidelines for Risk Management
Risk management is a cornerstone of the NIST Cybersecurity Framework. The framework provides guidelines on how to identify, assess, and prioritize cybersecurity risks. This risk assessment enables organizations to make informed decisions about which security controls to implement and how to allocate resources effectively. The NIST framework advocates for a continuous risk assessment process, ensuring that cybersecurity practices remain aligned with the evolving cybersecurity threat landscape. This proactive approach to managing cybersecurity is essential for maintaining a strong cybersecurity posture.
ISO 27001 and Other Top Cybersecurity Frameworks
Comparison with ISO 27001
The NIST Cybersecurity Framework is often compared to ISO 27001, another leading security framework for information security management. While both aim to help organizations manage cybersecurity, they differ in their approach to managing cybersecurity. The NIST CSF provides a flexible, risk assessment-based framework, whereas ISO 27001 is a more prescriptive security standard that requires certification. Both frameworks offer valuable guidance, but the choice depends on the organization's specific needs, regulatory requirements, and cybersecurity governance goals. Organizations may choose to align with both to achieve a comprehensive cybersecurity framework.
Benefits of Integrating Multiple Frameworks
Integrating multiple top cybersecurity frameworks, such as the NIST Cybersecurity Framework and ISO 27001, can offer significant benefits for an organization’s cybersecurity posture. By combining the strengths of different frameworks, organizations can achieve a more comprehensive cybersecurity framework approach to managing cybersecurity and addressing cybersecurity risk. For instance, the NIST CSF can be used to identify and prioritize cybersecurity risks, while ISO 27001 provides a structured approach to managing cybersecurity and implementing security controls. This integrated cybersecurity program enhances data security and overall cybersecurity posture.
Choosing the Right Framework for Your Organization
Choosing the right cybersecurity framework for your organization’s cybersecurity depends on several factors, including the organization’s size, industry, regulatory requirements, and cybersecurity risk profile. The NIST Cybersecurity Framework is a versatile option suitable for various sectors, offering a flexible, risk-driven approach to managing cybersecurity. ISO 27001 may be preferred by organizations seeking certification and a more structured security standard. Performing a thorough risk assessment and understanding your specific needs is crucial in selecting the best practice cybersecurity framework to help organizations improve its cybersecurity posture.