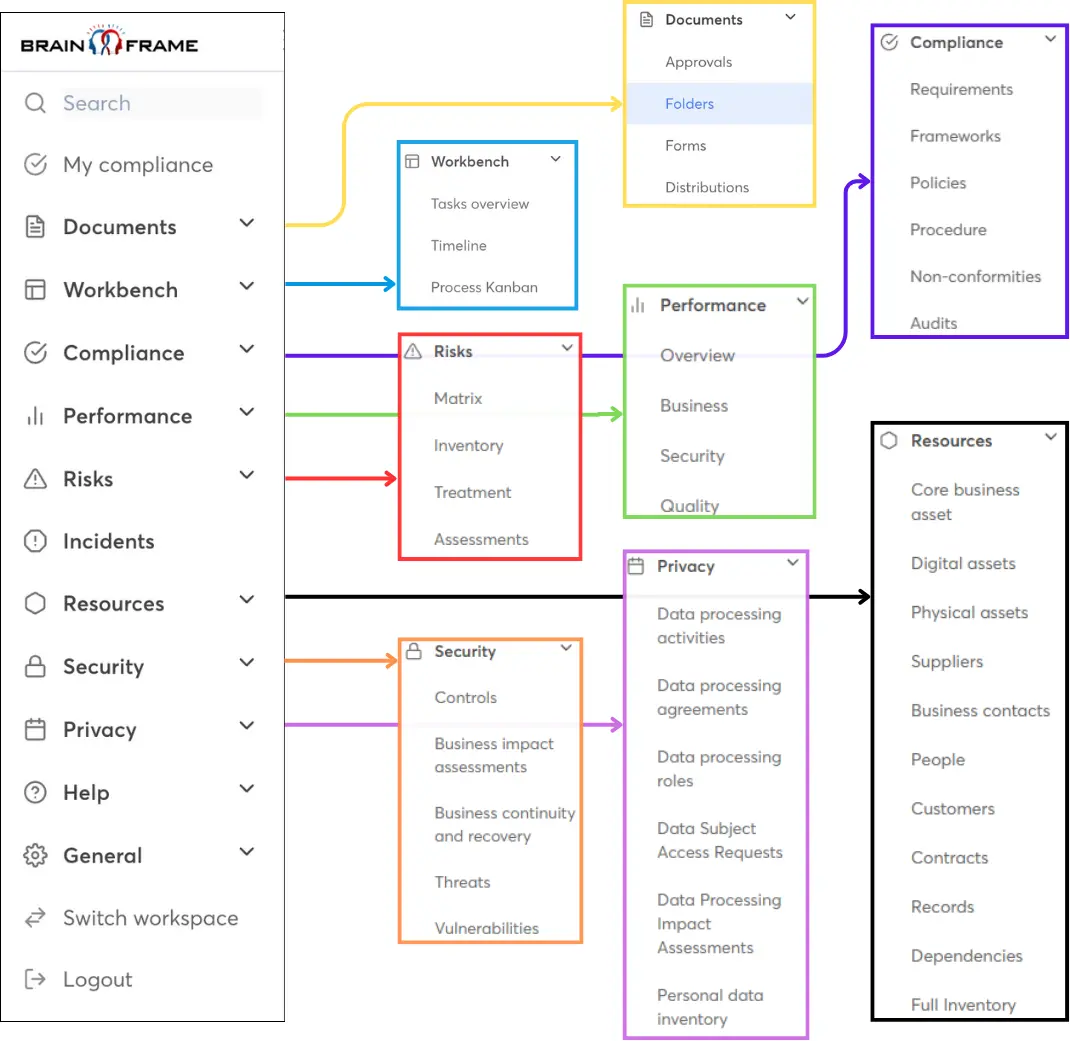
Streamline your GRC work using our all-in-one management solution and get access to our network of local specialists
Be the first to find out all the latest news,
products, and resources we are sharing.
By subscribing, you agree to receive occasional news and updates from us. We will process your personal data in accordance with our Privacy Policy
Thanks for registering!
Allow the use of cookies from this website on this browser?
We use cookies to provide improved experience on this website. You can learn more about our cookies and how we use them in our Cookie Policy.