The Rise of OT in Critical Sectors
Operational Technology (OT) has quietly powered the backbone of industries for decades. Think assembly lines in manufacturing, control systems in power plants, traffic management, and hospital equipment. Once siloed and isolated, these systems are now increasingly connected to corporate IT networks and even the cloud. The result? A massive expansion of the attack surface.
- Energy providers rely on OT for grid management.
- Hospitals use OT to monitor patient equipment.
- Transportation systems depend on OT to keep trains and planes on schedule.
When OT fails, the consequences can be catastrophic. Blackouts, halted production, grounded flights, or even patient safety risks.
The Wake-Up Calls
The world didn’t fully grasp how vulnerable OT could be until high-profile cyber incidents started hitting headlines:
- Stuxnet showed how OT can be weaponized.
- Colonial Pipeline (2021) left millions without fuel supply in the U.S.
- Norsk Hydro (2019) had to switch to manual operations after ransomware shut down factories.
Attackers have realized that disrupting physical processes creates maximum leverage. It forces quick pay-outs and causes chaos that ripples beyond the organization. Governments and regulators are watching closely, and so are cybercriminals.
In short: OT security has become a national concern, not just a corporate one.
Unique Challenges in OT Security
Legacy Systems That Refuse to Retire
Most OT environments run on equipment that’s been in place for years, if not decades. These systems were built for durability, not cybersecurity. Updating or patching them isn’t as simple as hitting “update now.” In many cases, vendors no longer even support the hardware or software. The result: unpatched vulnerabilities linger for years, waiting for an attacker to exploit.
- Long life cycles: OT gear is expected to run 20–30 years.
- Unsupported systems: Vendors stop issuing patches after a few years.
- Risk of downtime: Patching often means shutting down production, which is unacceptable in many cases.
Priorities: Safety and Availability Over Confidentiality
In the world of IT, we talk endlessly about confidentiality and data privacy. In OT, there’s a different priority: availability and safety. An outage on the factory floor can mean halted production lines or dangerous safety conditions. This makes traditional IT security measures hard to apply.
- Safety first: Worker protection takes priority.
- Always-on operations: Downtime equals huge financial and reputational loss.
- Security trade-offs: Stricter controls sometimes conflict with operational needs.
The Human Factor: More People, More Risk
Unlike IT environments with centralized access controls, OT often involves a parade of contractors, maintenance teams, and engineers. Each one may need physical or digital access to sensitive systems, sometimes with limited oversight.
- Third-party access: Temporary staff often get broad privileges.
- Limited training: OT staff may not have a cybersecurity background.
- Shared credentials: In some plants, “one password fits all” is still common.
These unique challenges mean standard IT security playbooks don’t work in OT. You can’t just roll out patches or force multi-factor authentication everywhere. Instead, organizations need a tailored approach that respects operational realities while raising the security baseline.
Compliance and Regulatory Drivers
A Web of Rules and Standards
As cyberattacks on OT environments escalate, regulators have stepped in with a patchwork of frameworks and directives. Companies that once only worried about uptime now face strict legal obligations. Falling behind can mean fines, lawsuits, and reputational scars.
Some key drivers:
- NIS2 Directive: Expands requirements for critical sectors, demanding risk assessments, incident reporting, and board-level accountability.
- DORA (Digital Operational Resilience Act): Targets the financial sector, but with clear implications for OT-heavy infrastructures supporting banking and payments.
- IEC 62443: The de facto standard for industrial control systems, guiding secure development and deployment.
- ISO 27001: Still relevant, but organizations must adapt it to OT realities.
More Than a Checkbox Exercise
Unlike IT, where regulatory lapses often mean data loss, failures in OT can halt national infrastructure or jeopardize public safety. This has regulators leaning toward real-time accountability.
- Mandatory incident reporting within 24–72 hours.
- Evidence of continuous monitoring, not just annual reviews.
- Board liability, making executives personally accountable for failures.
Meeting these obligations requires:
- Clear governance structures between IT and OT teams.
- Documented risk management processes tailored to physical systems.
- Vendor oversight, since third parties often control or maintain OT systems.
Risk Management in the OT Context
Mapping the Invisible Web
Unlike IT, where assets are well-documented (hopefully), OT environments are notoriously opaque. Many organizations don’t have a clear inventory of what’s connected to their networks. Hidden dependencies between sensors, controllers, and legacy systems create a domino effect: compromise one small device, and you may disrupt the entire production line.
Key first steps:
- Asset discovery: Identify every controller, sensor, and interface.
- Dependency mapping: Understand how failures cascade through systems.
- Criticality ranking: Prioritize what truly keeps the business running.
Threats That Hit Different
Cyber risks in OT go beyond stolen data. They strike at the physical core of operations. Attackers may not care about customer records — they care about halting pumps, shutting valves, or corrupting safety alarms.
OT-specific risks include:
- Sabotage of production processes.
- Supply chain attacks targeting vendors or contractors.
- Ransomware that locks operators out of control systems.
- Insider threats from contractors with elevated access.
Balancing Security and Continuity
The dilemma is: security measures that work in IT can disrupt OT workflows. A firewall rule or patch that seems harmless might crash a decades-old control system. Therefore, businesses must seek a delicate balance between tightening defenses and ensuring uninterrupted operations.
Practical approaches:
- Segment networks to contain attacks without shutting down entire plants.
- Use compensating controls where patching is impossible.
- Scenario testing to gauge how incidents play out in real time.
Why Risk Management Must Evolve
Traditional, spreadsheet-based risk assessments can’t capture the complexity of OT systems. Effective risk management requires dynamic, ongoing monitoring that reflects the realities of industrial environments.
Incident Response and Business Continuity
In IT, a delayed response to a breach may lead to data leaks. In OT, even a short delay can halt production lines, disrupt energy grids, or endanger lives. Incident response in OT is therefore less about PR damage control and more about keeping the lights on and operations safe.
The Complexity of OT Incidents
Responding to an OT security event isn’t like flipping through a playbook. Each incident brings unique challenges:
- Mixed ownership: IT security teams, engineers, and external contractors all share responsibility.
- Physical safety considerations: Decisions must ensure worker and public safety first.
- Regulatory clock ticking: Many rules (e.g., NIS2) demand notifications within 24–72 hours.
This blend of urgency, complexity, and oversight makes coordination a real challenge.
Crisis Communication Done Right
When OT systems fail, stakeholders that are waiting for updates can include:
- Regulators, expecting timely and detailed reports.
- Partners and suppliers, who may also be impacted.
- Customers and the public, often quick to panic if left in the dark.
Without a structured communication plan, confusion can spread faster than the incident itself.
Building True Continuity
Business continuity in OT goes beyond backup servers. It must ensure that physical processes keep running safely. Organizations should:
- Maintain redundant systems for critical functions.
- Conduct tabletop exercises simulating OT-specific attacks.
- Establish cross-functional response teams bridging IT and OT.
A strong incident response and continuity plan can mean the difference between a brief disruption and a national headline. In OT, preparation can mean survival.
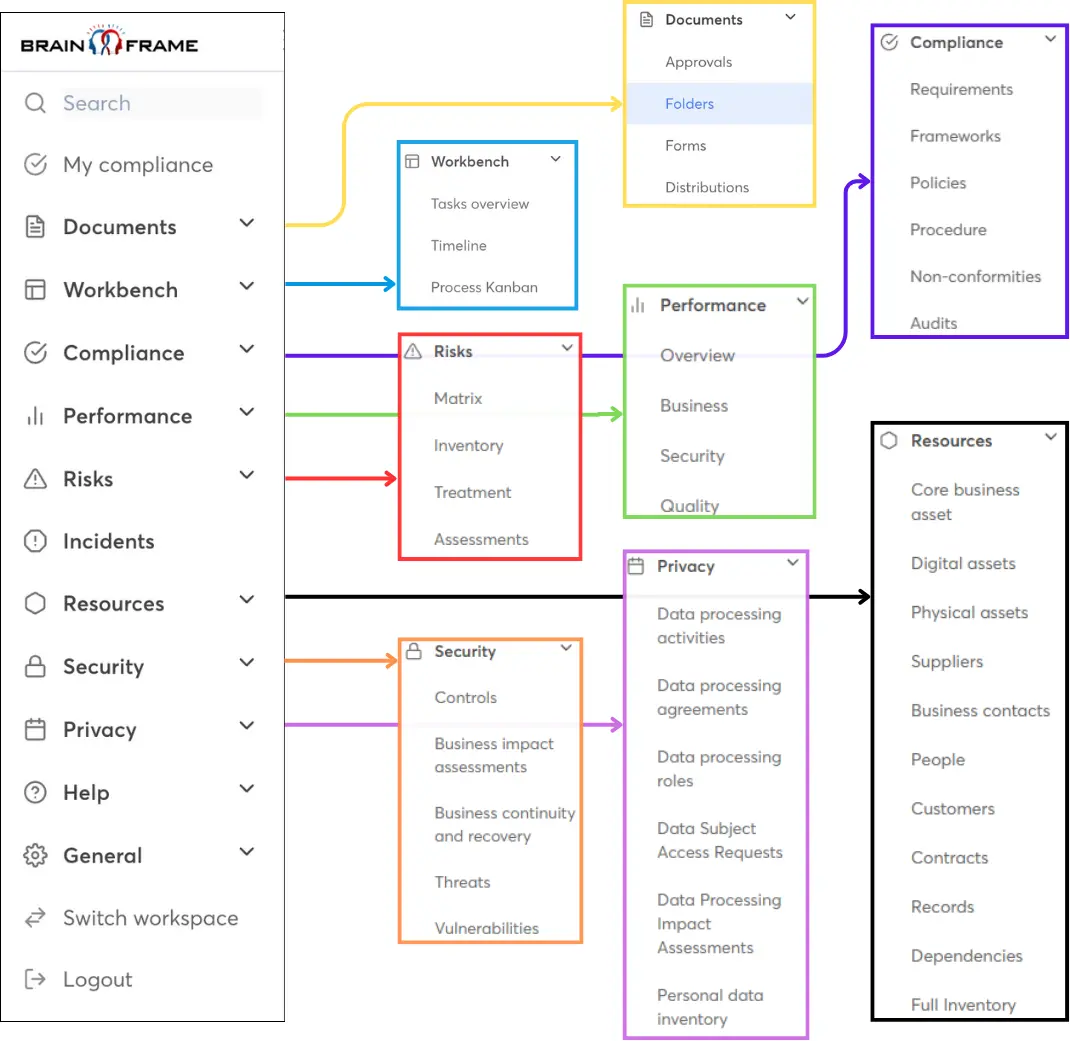
How Brainframe Can Help
Turning Complexity Into Structure
Operational Technology security requires governance, risk management, and incident readiness that fit the realities of industrial environments. This is where Brainframe steps in, transforming spreadsheets and processes into a centralized, actionable framework.
Risk Register for OT and IT
Brainframe’s risk management feature allows organizations to:
- Document and monitor critical OT assets alongside IT infrastructure.
- Map dependencies so risks are evaluated in context, not in isolation.
- Prioritize mitigation steps with a clear view of what keeps operations running.
Instead of juggling spreadsheets, security teams gain a dynamic register.
Incident Reporting That Matches Regulatory Demands
When incidents happen, time is short and regulators expect answers fast. Brainframe provides:
- Customizable incident templates that can be tailored to NIS2, ISO 27001, and other frameworks.
- Reporting workflows for quick escalation and compliance-ready records.
- Audit trails to prove that correct procedures were followed.
This means your response is both faster and better documented.
Vendor and Contractor Oversight
With many OT incidents linked to third parties, Brainframe’s vendor management features make it easier to:
- Track supplier compliance with cybersecurity requirements.
- Collect evidence from vendors through structured forms.
- Ensure maintenance contractors follow security-by-design principles.
Governance Without the Guesswork
Brainframe simplifies compliance by embedding policy management, control mapping, and documentation into a single platform. Whether you’re preparing for NIS2 audits or aligning with IEC 62443, everything is centralized and easy to maintain.
OT security is a high-stakes game where mistakes have real-world consequences. With Brainframe, organizations can bridge the gap between IT and OT security, ensuring resilience, compliance, and continuity — without adding complexity.
Quick actions you can take today
Strengthening Operational Technology security doesn’t always require a massive overhaul on day one. Companies can start small, but smart. Here are some practical steps you can take immediately:
-
Build a basic OT asset inventory
Even a high-level list of critical machines, sensors, and control systems gives you visibility you may not have today. Knowing what you’re protecting is the first step toward effective risk management. -
Run an incident simulation
Gather IT, OT, and management teams for a tabletop exercise. Walk through what would happen if a key system failed or was hit with ransomware. This helps reveal blind spots in your incident response plan. -
Engage your third parties
Many OT risks come through contractors, integrators, or suppliers. Begin by requesting evidence of their cybersecurity practices — certificates, policies, or recent audits. This sets expectations and reduces supply chain risk. -
Establish communication lines
In an OT crisis, confusion can cost precious time. Define now who talks to regulators, who handles technical remediation, and who updates stakeholders. Clear roles prevent chaos later. -
Kick-start governance
Appoint a cross-functional team that includes IT security, OT engineers, and compliance officers. Even a lightweight committee can make sure decisions don’t fall through the cracks.
These quick wins won’t solve every challenge, but they create momentum. By taking visible, measurable steps today, organizations can lay the groundwork for stronger resilience tomorrow.