Single sign-on SSO with SAML
Using Single Sign-On (SSO) with Security Assertion Markup Language (SAML) offers several significant benefits, making it a popular choice for enhancing both security and user experience in Brainframe:
- Enhanced Security: SSO with SAML reduces the number of attack surfaces by minimizing the need for multiple passwords. Since users only need to remember one set of credentials, they are more likely to use stronger, unique passwords, reducing the risk of password-related breaches.
- Improved User Experience: SSO streamlines the login process, allowing users to access multiple applications or services with a single authentication process. This eliminates the need for remembering multiple passwords, leading to a smoother, more efficient user experience.
- Simplified Credential Management: For administrators, SSO with SAML simplifies the management of user credentials. It centralizes the authentication process, making it easier to implement and enforce security policies, and to manage user access across different systems.
- Reduced IT Overhead: By reducing the number of login credentials users need to remember, SSO with SAML significantly decreases the volume of password reset requests, which can be a major burden on IT resources.
- Interoperability and Flexibility: SAML is an open standard, meaning it is designed to work across different systems and platforms. This interoperability ensures that SSO can be implemented in a wide variety of environments, providing flexibility in integrating with new applications and services.
- Audit and Compliance Benefits: SSO with SAML provides centralized logging of user activities, which is invaluable for audit trails and compliance with various regulations. It makes it easier to monitor and report on who is accessing what and when, enhancing overall organizational compliance.
Configuration
Only users with administrator rights can access the Authentication menu in the workspace settings page
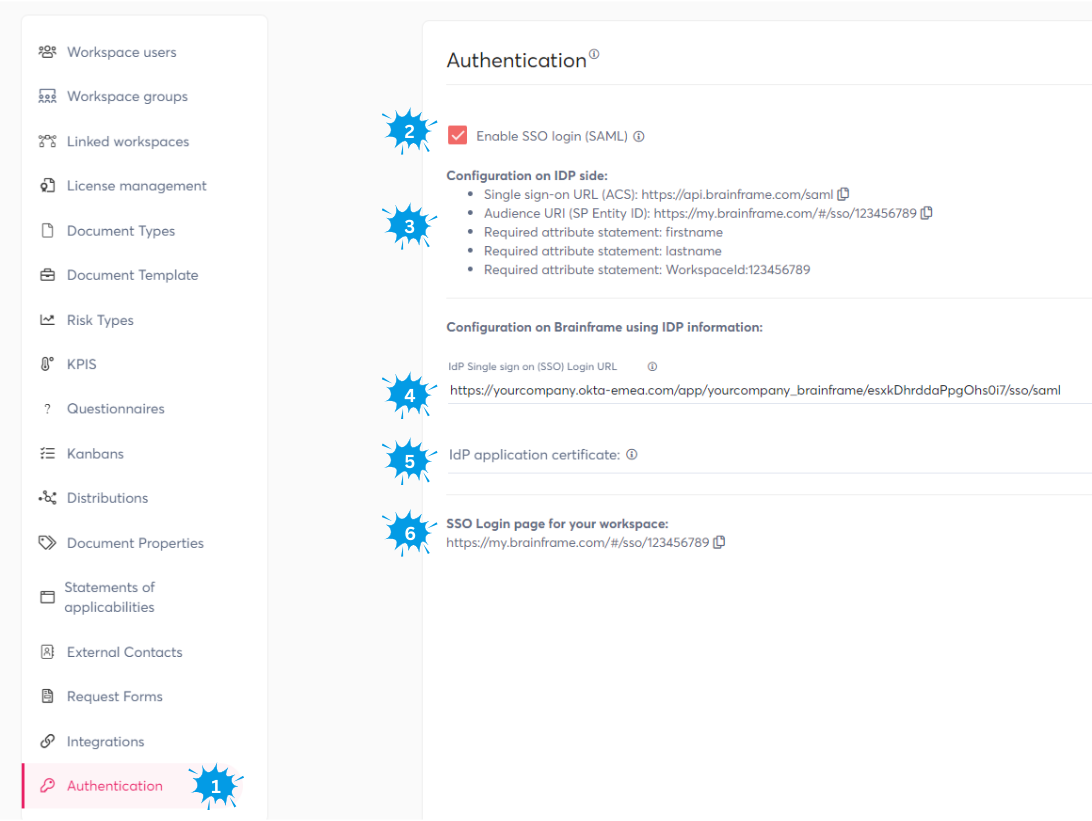
- Open the authentication menu in the Settings page
- Enable SSO with Saml by checking this checkbox
- On your identity provider (e.g. Okta, Azure, JumpCloud, ...) you need to create a new SAML application with the following configurations
- Single sign-on URL (ACL) - This is the link where your identity provider will communicate with Brainframe
- Audience URI (SP Entity ID) - This is the unique identifier of your workspace on the Brainframe side
- User attribute configurations allowing users to be auto create on Brainframe side with first login (email is automatically passed as unique user attribute)
- firstname
- lastname
- WorkspaceId (case sensitive) - This needs to be set to the Workspace identifier. Simply copy/paste the value suggested by Brainframe
- IdP Single sign on (SSO) Login URL: This is the value generated by your identity provider specifically for the app you created in step 3. It allows Brainframe to know where to send users that are not authenticated
- IdP application certificate: This is the certificate generated by your identity provider specifically for the app you created in step 3. It allows Brainframe to verify that the SAML claims are effectively created/signed by your identity provider
- This is a link you can put in your intranet, allowing users to directly log into your workspace with only a button "Login with SSO" that opens/verifies the login of your IdP
INFO
SSO SAML sessions automatically expire after 8h of non-activity on Brainframe to accommodate for deactivations on IdP level.
ATTENTION
Users logged in using SSO SAML can only switch to other workspaces that have been configured with the same identity provider
Automatic user creation & rights
Every user you assign to your own identity provider, will be able to log into Brainframe. When a user does not exist, they are created without admin rights, and will only have access to their own INBOX folder. Using the folder permissions you can give these users access to existing folders. They will only see data of folders they have access to.